HTB Sherlock - TickTock Writeup
 HTB Sherlock - TickTock Writeup
HTB Sherlock - TickTock WriteupSherlock Scenario
Gladys is a new joiner in the company. She has received an email informing her that the IT department is due to do some work on her PC. She is guided to call the IT team, where they will inform her on how to allow them remote access. However, the IT team is actually a group of hackers attempting to attack Forela.
Artefacts
After unpacking the ZIP file, we get logs of collected artefacts in CSV format and copies of the most important files from the user’s C drive. The files include MFT, configuration files, event logs, Prefetch files, etc. In total, we receive about 990 files (Fig. 1).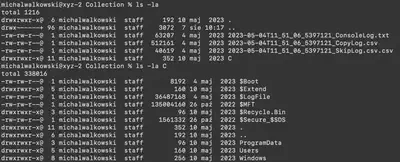
Solution
Task 1
What was the name of the executable that was uploaded as a C2 Agent?
After reviewing the contents of the directories, I decided to start my search by checking the contents of the MFT file. Using the MFT Explorer program, I opened the file and began browsing the files in the user’s home directory. On the user’s desktop, I noticed two standout files: the first was merlin.exe, which turned out to be a cross-platform C2 agent written in GO, and the PowerShell script Invoke-TimeWizard.ps1, which provided an immediate answer to Task 7 (Fig. 2).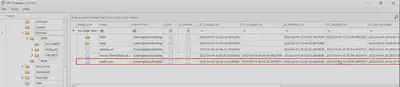
Answer: merlin.exe
Task 2
What was the session ID for the initial access?
From the task description, we learn that the attacker gained remote access to the computer after informing the employee. Analyzing the received files, I noticed that the directory C/Users/gladys/AppData/Local/ contains artefacts related to the TeamViewer application, which allows for easy and fast remote access to a computer.
During my work, I witnessed my colleague, who was conducting social engineering tests using TeamViewer, gain access to a victim’s computer. Therefore, I was immediately interested in the contents of this directory. There is a file called TeamViewer15_Logfile.log, which contains all the information regarding the attacker’s access. It was in this file that I found the answer regarding the session ID obtained by the attacker (Fig. 3). Additionally, in the same file, I also found information about the uploaded file merlin.exe and answers to two more tasks (Tasks 4 and 8).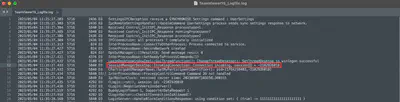
Answer: -2102926010
Task 3
The attacker attempted to set a BitLocker password on the C: drive. What was the password?
I assumed that the attacker tried to set the password using a PowerShell command. After executing the command target/release/chainsaw search --skip-errors "powershell" ../htb/Collection/C/Windows/ --timestamp 'Event.System.TimeCreated_attributes.SystemTime' --from "2023-05-04T11:35:00", I obtained all occurrences of PowerShell. I specifically added the time to limit the number of results, but there were still quite a few - 634 to be exact. However, finding the correct entry was surprisingly easy, as it stood out significantly from the others (Fig. 4).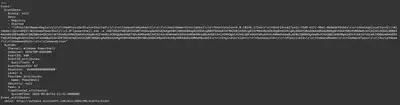
The entire command was encoded in base64. After decoding it using CyberChef and removing NULL, I obtained the password (Fig. 5).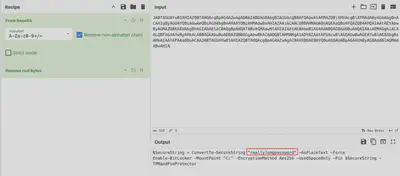
Answer: reallylongpassword
Task 4
What name was used by the attacker?
As I mentioned while solving Task 2, the same TeamViewer log TeamViewer15_Logfile.log contains the name used by the attacker (Fig. 6).
Answer: Fritjof Olfasson
Task 5
What IP address did the C2 connect back to?
Using the command chainsaw search --skip-errors "merlin.exe" ../htb/Collection/C/Windows/, I retrieved all events triggered by the merlin.exe agent. In almost each of these events, there is the IP address to which the agent connected (Fig. 7).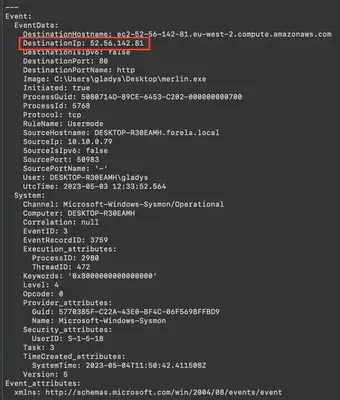
Answer: 52.56.142.81
Task 6
What category did Windows Defender give to the C2 binary file?
Reviewing the files collected as artefacts in the directory C/ProgramData/Microsoft/Windows Defender/Support, I noticed available log files from Windows Defender. My attention was drawn to the file MPLog-07102015-052145.log. As can be seen, the file name refers to a date from the past, suggesting that the attacker changed the system date multiple times. Since this is a binary file, I used the command strings -e l "C/ProgramData/Microsoft/Windows Defender/Support/MPLog-07102015-052145.log" | grep merlin.exe to find all occurrences of merlin.exe. The result of this command allowed me to find the answer to this task and to Task 9 (Fig. 8).
Answer: VirTool:Win32/Myrddin.D
Task 7
What was the filename of the PowerShell script the attackers used to manipulate time?
I found the answer to this task while solving Task 1. Reviewing the contents of the MFT, I noticed two files on the user’s desktop: merlin.exe and Invoke-TimeWizard.ps1. The name Invoke-TimeWizard.ps1 immediately suggests that it is a script responsible for time modifications in the system. Additionally, checking the file’s contents, I noticed PowerShell commands responsible for time modifications, confirming that this is the file I was looking for (Fig. 9).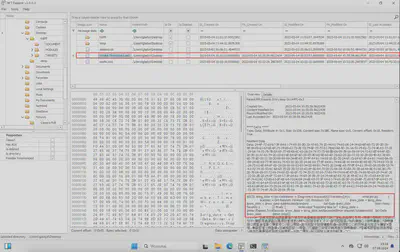
Answer: Invoke-TimeWizard.ps1
Task 8
What time did the initial access connection start?
The question was a bit tricky, as the order of this task misled me. Usually, the question about the time of the attacker’s connection refers to C2. It took me a moment to understand that it was about the first connection made by the attacker. The first connection was made through TeamViewer (Fig. 10).
Answer: 2023/05/04 11:35:27
Task 9
What is the SHA1 and SHA2 sum of the malicious binary?
I found the answer to this question while solving Task 6 (Fig. 11).
Answer: ac688f1ba6d4b23899750b86521331d7f7ccfb69:42ec59f760d8b6a50bbc7187829f62c3b6b8e1b841164e7185f497eb7f3b4db9
Task 10
How many times did the PowerShell script change the time on the machine?
The event ID responsible for time change is 4616. Using the command chainsaw search -t 'Event.System.EventID: =4616' --skip-errors C/Windows/System32, I searched for all events. It turned out that the number 2374 is not the correct answer (Fig. 12).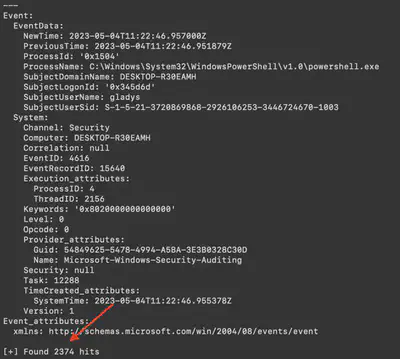
SystemSettingsAdminFlows.exe (Fig. 13). However, I was only interested in the events related to the time change using the previously found script, which was executed via PowerShell.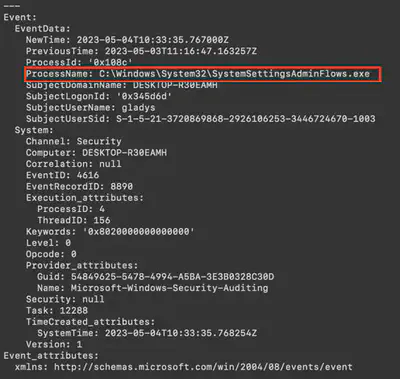
SystemSettingsAdminFlows.exe.grep and wc -l provided me with the correct number of time changes made by the attacker (Fig. 14).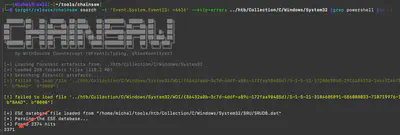
Answer: 2371
Task 11
What is the SID of the victim user?
The answer to this question is found in every event that included the username. Therefore, while solving the previous tasks, I copied the user’s SID (Fig. 15).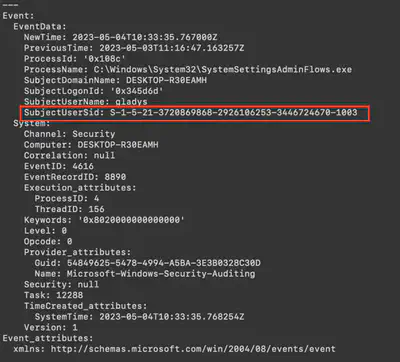
Answer: S-1-5-21-3720869868-2926106253-3446724670-1003