HTB Sherlock - Subatomic Writeup
 HTB Sherlock - Subatomic Writeup
HTB Sherlock - Subatomic WriteupSherlock Scenario
Forela is in need of your assistance. They were informed by an employee that their Discord account had been used to send a message with a link to a file they suspect is malware. The message read: “Hi! I’ve been working on a new game I think you may be interested in it. It combines a number of games we like to play together, check it out!”. The Forela user has tried to secure their Discord account, but somehow the messages keep being sent and they need your help to understand this malware and regain control of their account! Warning: This is a warning that this Sherlock includes software that is going to interact with your computer and files. This software has been intentionally included for educational purposes and is NOT intended to be executed or used otherwise. Always handle such files in isolated, controlled, and secure environments. Once the Sherlock zip has been unzipped, you will find a DANGER.txt file. Please read this to proceed.
Artifacts
After extracting the ZIP file, we find two files: DANGER.txt and malware.zip. The DANGER.txt file contains a warning about the contents of the ZIP file and the password needed to extract malware.zip. After extracting malware.zip, we get a file named nsis-installer.exe, which is the malware we need to analyze to solve the tasks (Fig. 1).
Solution
Task 1
What is the Imphash of this malware installer?
The first step I took to analyze the malware was to use VirusTotal. In the “Details” tab, I found the answer to the first question (Fig. 2).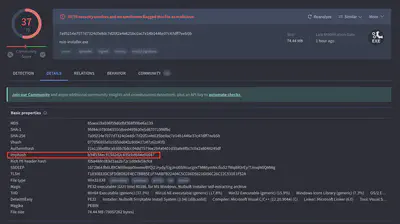
Answer: b34f154ec913d2d2c435cbd644e91687
Task 2
The malware contains a digital signature. What is the program name specified in the SpcSpOpusInfo Data Structure?
I also found the answer to this question on VirusTotal (Fig. 3).
SpcSpOpusInfo section on VirusTotal.
Answer: Windows Update Assistant
Task 3
The malware uses a unique GUID during installation, what is this GUID?
At first, I tried to analyze the file using PE-bear, but it did not yield any results. So I returned to the analysis on VirusTotal. There, I noticed that it is a “Nullsoft Installer self-extracting archive.” Using this article, I found out that this is an archive that can be extracted using 7z. Initially, I tried to use 7z available from the manufacturer’s website (Fig. 4).
nsis-installer.exe file, no .nsi file found.
nsis-installer.exe file, using 7zip available in FlareVM.[NSIS].nsi file, which is responsible for the steps taken during the installation of the malware, I found the GUID I was looking for (Fig. 6).![Fig. 6. Found GUID in the <code>[NSIS].nsi</code> file.](/post/sherlock-subatomic/figure_task_3_2_hu530f80bc38ab51ea6709e3036ab7b6e9_238204_42368642519d7d4fce72a9310b8862f1.webp)
[NSIS].nsi file.
Answer: cfbc383d-9aa0-5771-9485-7b806e8442d5
Task 4
The malware contains a package.json file with metadata associated with it. What is the ‘License’ tied to this malware?
In the $PLUGINSDIR directory, I found another archive, app-32.7z (Fig. 7).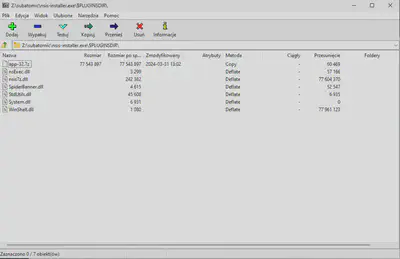
$PLUGINSDIR directory.package.json file. The package.json file is used by the npm package manager, which suggested to me that I was looking for something related to JavaScript. Typically, JavaScript-related files are placed in separate directories, such as resources or static. In this case, I found a resources directory in the archive (Fig. 8).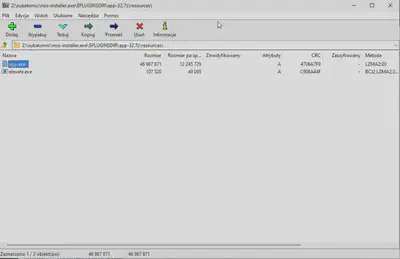
app-32.7z archive, resources directory.elevate.exe and app.asar. After searching Google, I found that files with the .asar extension are another archive format that works similarly to tar (link). Using the command npm install --engine-strict @electron/asar, available in the Readme.md file of this package, I installed the asar software. Then, using the command asar e app.asar ./resources/, I extracted all the files from the archive (Fig. 9).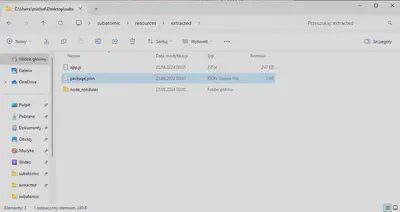
app.asar archive.package.json file, I got the answer (Fig. 10).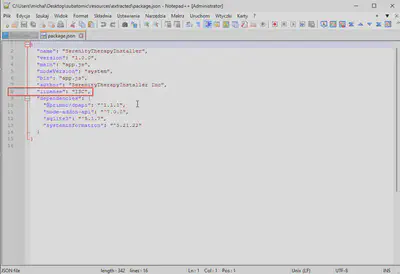
package.json file.
Answer: ISC
Task 5
The malware connects back to a C2 address during execution. What is the domain used for C2?
I obtained the answer to this question during the initial analysis using VirusTotal (Fig. 11).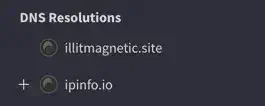
Answer: illitmagnetic.site
Task 6
The malware attempts to get the public IP address of an infected system. What is the full URL used to retrieve this information?
The file containing the malicious code is located in app.js. The entire file is obfuscated and difficult to read (Fig. 12). Initially, I tried manual deobfuscation and also used ChatGPT, but both methods were unsuccessful. Therefore, I decided to try dynamic analysis.
primno/dpapi package (Fig. 13).
app.js.primno directory in node_modules and reinstalled the package using the command npm install @primno/dpapi. Unfortunately, the next attempt to run the script also failed. This time the problem was with the sqlite3 dependency (Fig. 14). I took the same step as before, deleting the sqlite3 directory from node_modules, and then reinstalling the dependency using the command npm install sqlite3.
app.js.eval, I found the deobfuscated app.js script (Fig . 15).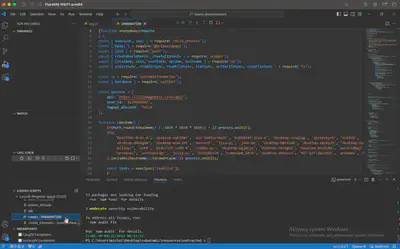
ipinfo.io domain (Fig. 16).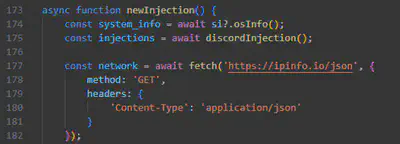
Answer: https://ipinfo.io/json
Task 7
The malware is looking for a particular path to connect back on. What is the full URL used for C2 of this malware?
After obtaining the deobfuscated content of the app.js script, the answer to this question I found in line 14 (Fig. 17).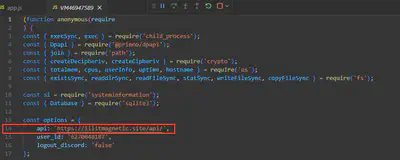
Answer: https://illitmagnetic.site/api/
Task 8
The malware has a configured user_id which is sent to the C2 in the headers or body on every request. What is the key or variable name sent which contains the user_id value?
After obtaining the deobfuscated content of the app.js script, the answer to this question I found in line 45 (Fig. 18).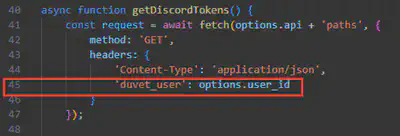
Answer: duvet_user
Task 9
The malware checks for a number of hostnames upon execution, and if any are found it will terminate. What hostname is it looking for that begins with arch?
Using the file search function, I found only one instance of the word arch (Fig. 19).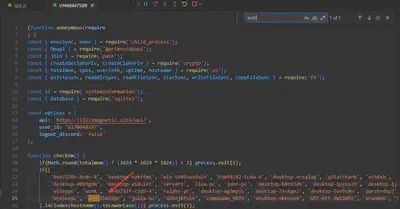
arch.
Answer: archibaldpc
Task 10
The malware looks for a number of processes when checking if it is running in a VM; however, the malware author has mistakenly made it check for the same process twice. What is the name of this process?
The checkVM function retrieves a list of processes using the tasklist command and then checks if any from the following list appear on that list. Upon closer inspection, I noticed that the repeated value is vmwaretray (Fig. 20).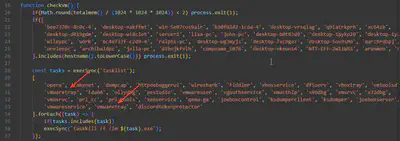
Answer: vmwaretray
Task 11
The malware has a special function which checks to see if C:\Windows\system32\cmd.exe exists. If it doesn’t it will write a file from the C2 server to an unusual location on disk using the environment variable USERPROFILE. What is the location it will be written to?
Once again using the file search function, I started by searching for all occurrences of cmd.exe. This way, I found the checkCmdInstalation function. This function checks if the cmd.exe file exists in the C:\Windows\system32\cmd.exe location. If the file does not exist, it downloads and saves it to %USERPROFILE%\Documents\cmd.exe (Fig. 21).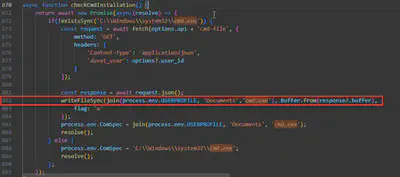
Answer: %USERPROFILE%\Documents\cmd.exe
Task 12
The malware appears to be targeting browsers as much as Discord. What command is run to locate Firefox cookies on the system?
Using the file search function, I found the getFirefoxCookies function. In line 496, a system command is executed that searches for files containing cookies for Firefox (Fig. 22).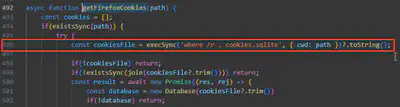
Answer: where /r . cookies.sqlite
Task 13
To finally eradicate the malware, Forela needs you to find out what Discord module has been modified by the malware so they can clean it up. What is the Discord module infected by this malware, and what’s the name of the infected file?
As in previous cases, I first used the file search function. This led me to find the discordInjection function. This function scans the system for installed versions of Discord, then locates and modifies the index.js file in the discord_desktop_core-1 directory (module) (Fig. 23).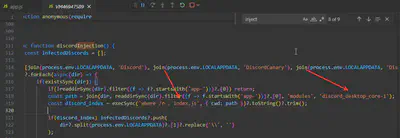
Answer: discord_desktop_core-1, index.js