HTB Sherlock - ProcNet Writeup
 HTB Sherlock - ProcNet Writeup
HTB Sherlock - ProcNet WriteupSherlock Scenario
With the rising utilization of open-source C2 frameworks by threat actors, our red team has simulated the functionalities of one such widely employed framework. The objective of this exercise is to aid blue teams in strengthening their defenses against these specific threats. We have been provided with PCAP files and APIs collected during the event, which will serve as valuable resources.
Artifacts
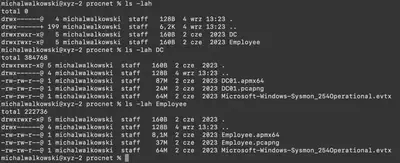
To solve the task, we are provided with two directories (Fig. 1):
DC- contains artifacts collected from the domain controller, such as a traffic dump (pcapng), API call registry (apmx64), and Sysmon event logs (evtx),Employee- contains the same artifacts, this time collected from an employee’s computer, which the attackers initially accessed.
Solution
Task 1
To which IP address and port number is the malware attempting to establish a connection?
The task indicates that the employee was targeted first. Therefore, I started the search by analyzing the contents of the Employee.pcapng file. To identify which IP addresses are involved in the traffic flow, I first tried to determine which IP addresses exchanged the most data. For this purpose, I used the “Conversations” tab. I noticed two prominent IP addresses: 3.6.165.8 and 10.10.0.79, which exchanged 17,069 packets between them, distinguishing them from the others (Fig. 2).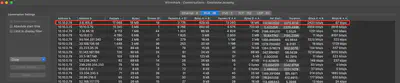
csgo.exe, which is likely malicious software (Fig. 4).
At this point, I knew that the IP address 10.10.0.79 belonged to the employee. The next task indicated that communication between the malware and the C2 server uses encrypted communication. First, I used filters to exclude communication on port 8080, leaving only ports 80 and 443. Communication on port 80 was too short and was related to an attempt to invoke a registration form. Communication using port 443 seemed to be the one I was currently looking for.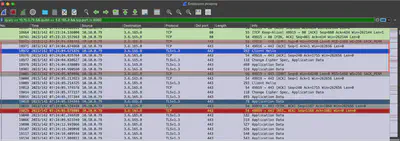
Answer: 3.6.165.8:443
Task 2
Now that you are aware of the IP address and port number, what is the JA3 fingerprint of the C2 server?
Firstly, I checked what a JA3 fingerprint is. From this article, I learned that it is a fingerprint for SSL/TLS clients. I found the JA3 fingerprint in the first TLS Client Hello packet sent by the client (Fig. 6).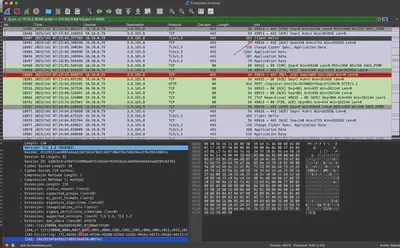
Answer: 19e29534fd49dd27d09234e639c4057e
Task 3
What is the name of the C2 framework being utilized by the red team?
After finding the JA3 fingerprint, I was able to quickly determine the C2 server’s name. The results showed silver (Fig. 7).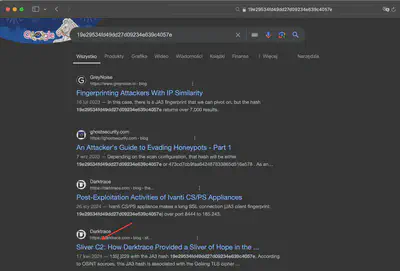
Answer: sliver
Task 4
Which WIN32 API provided the red team with the current directory information?
I had previously familiarized myself with apmx64 files while solving another Sherlock task, Jugglin. After launching API Monitor, I started examining API calls from the malicious software csgo.exe. Reviewing the calls, I found GetCurrentDirectoryW right at the beginning of the program’s execution (Fig. 8).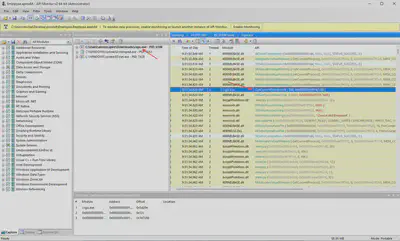
Answer: GetCurrentDirectoryW
Task 5
Now that we have identified the C2 framework utilized by the red team, which C2 command is responsible for opening notepad.exe by default and loading the .NET CLR into it?
In this case, I also used Google search (Fig. 9). The first link led to an article, where I found that the command used to load .NET libraries is execute-assembly.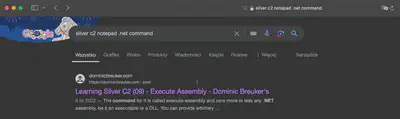
Answer: execute-assembly
Task 6
What is the name of the module (DLL) that was loaded to gain access to Windows Vault?
The next step taken by the attackers was to launch the notepad.exe process and load an additional library for communication with Windows Vault. To identify this library, I selected the process and expanded the Modules tab. On the list of loaded modules, only one had vault in its name (Fig. 10).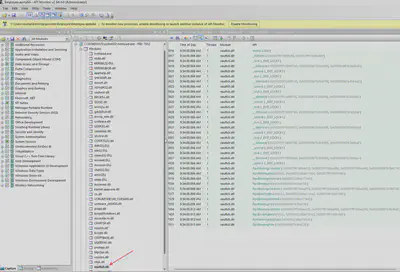
notepad.exe process for Windows Vault handling.
Answer: vaultcli.dll
Task 7
After loading the mentioned module, there were a series of WIN32 APIs loaded. Which specific Win32 API is responsible for enumerating vaults?
Reviewing API calls made by the notepad.exe process, immediately after loading the Windows Vault handling library, I found an API call responsible for enumeration (Fig. 11).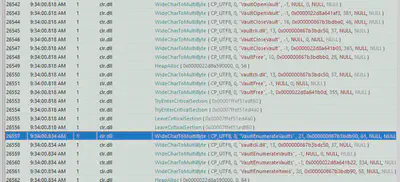
Answer: VaultEnumerateVaults
Task 8
Which command did the attacker execute to identify domain admins?
The last process registered by API Monitor in the Employee.apmx64 file is net. The net command in Windows is primarily used to manage network resources. When selecting the process from the list, the command executed by the attacker appears right at the beginning (Fig. 12).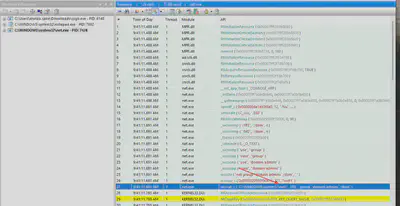
Answer: net group "domain admins" /dom
Task 9
The red team has provided us with a hint that they utilized one of the tools from “ARMORY” for lateral movement to DC01. What is the name of the tool?
Among the libraries loaded by csgo.exe, I found an additional library wminets_utils.dll, which is associated with remote WMI execution (Fig. 13).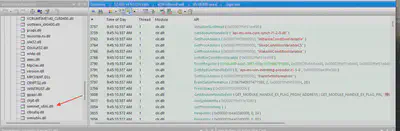
csgo.exe process imports the ExecQueryWmi function, indicating possible WMI usage (Fig. 14).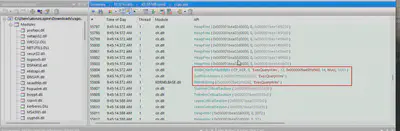
Searching for WMI-related strings, I came across SharpWMI (Fig. 15). Comparing the list of tools with this repository, I confirmed it is the tool I was looking for.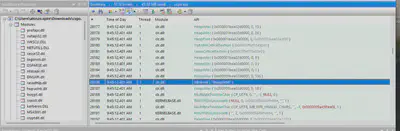
Answer: sharpwmi
Task 10
Which command was executed by the red team to extract/dump the contents of NTDS.DIT?
After performing lateral movement, the attackers proceeded to dump the contents of the NTDS.DIT file. Using API Monitor, I opened the second file DC01.apmx64 and then searched for NTDS-related phrases (Fig. 16).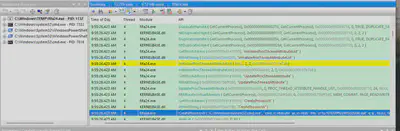
Answer: cmd /c ntdsutil "ac in ntds" ifm "cr fu %TEMP%\H00i0Z000.dat" q q
Task 11
The red team has obtained the aforementioned dump by compressing it into a ZIP file. Which specific Win32 API is responsible for retrieving the full path of the file to be downloaded?
Again using the search functionality, I checked each occurrence of .zip until I found the relevant API call (Fig. 17).
Answer: GetFullPathNameW