HTB Sherlock - Nuts Writeup
 HTB Sherlock - Nuts Writeup
HTB Sherlock - Nuts WriteupSherlock Scenario
HTB did not provide a scenario for the Sherlock challenge.
Artifacts
To solve the challenge, we receive a copy of the files from the user’s C drive. The total number of downloaded files is 317,824. In my opinion, this is the task with the largest number of files we have received in a DFIR challenge (Fig. 1).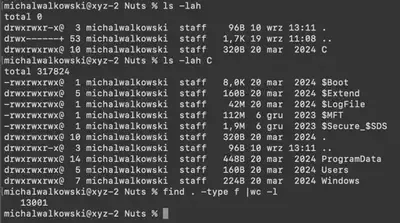
Solution
Task 1
What action did Alex take to integrate the purported time-saving package into the deployment process? (provide the full command)
In the Users directory, we find three user folders: Administrator, Default, and Public, which means Alex was likely working by default on the system administrator account. After looking into the Administrator directory, I immediately noticed a .nuggets folder, indicating that the user was using Nuggets software as a package manager for the .NET platform. From the task description, we know that the user executed a command on the system, so I focused on finding the history of executed commands using PowerShell. In the directory C/Users/Administrator/AppData/Roaming/Microsoft/Windows/PowerShell/PSReadline, there is a file ConsoleHost_history.txt, which contains the history of PowerShell commands executed by the user. This file contains the answer to the question (Fig. 2).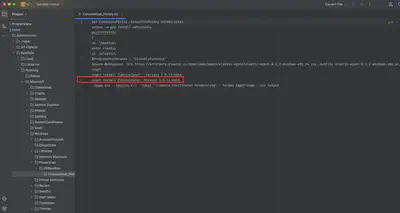
Answer: nuget install PublishIgnor -Version 1.0.11-beta
Task 2
Identify the URL from which the package was downloaded.
Since I already knew which package was downloaded, I initially thought I could find this information in NuGet’s cache files. However, my search turned out fruitless. I didn’t find what I was looking for there. So, I decided to find the path the user took to reach the malicious package. Likely, the user searched for this using a browser, so there should be some browsing history. In Chrome’s History file, I found an entry with a link (Fig. 3).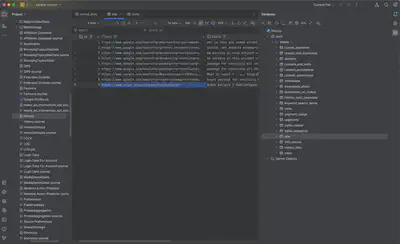
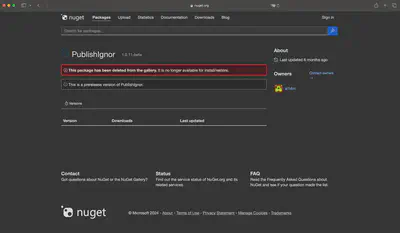
Answer: https://www.nuget.org/packages/PublishIgnor/
Task 3
Who is the threat actor responsible for publishing the malicious package? (the name of the package publisher)
The answer to this question was found during the solution to Task 2 (Fig. 4).
Answer: a1l4m
Task 4
When did the attacker initiate the download of the package? Provide the timestamp in UTC format (YYYY-MM-DD HH:MM).
In my opinion, the wording of this task is incorrect; it should have been: “when did the user download the malicious software.” I wasted a lot of time searching for the moment when the attacker enabled the download of the malicious software through NuGet. It turned out that the correct answer is the approximate time the user downloaded the software. I found this by checking the creation attributes of the folder using the MFTExplorer software (Fig. 5).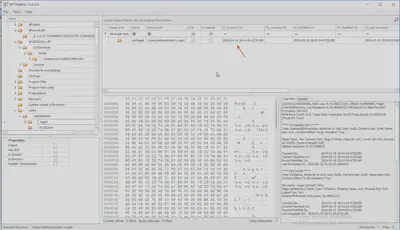
Answer: 2024-03-19 18:41
Task 5
Despite restrictions, the attacker successfully uploaded the malicious file to the official site by altering one key detail. What is the modified package ID of the malicious package?
To find the difference between the original package and the one created by the attacker, I first had to find the legitimate one. After a brief search, I found the correct package on NuGet. What immediately caught my eye was the package name. The attacker omitted the letter e in the name while creating the malicious package. By doing this, they created a new package ID and were able to upload it to the site, allowing it to be downloaded (Fig. 6).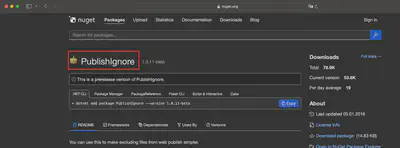
Answer: PublishIgnor
Task 6
Which deceptive technique did the attacker employ during the initial access phase to manipulate user perception? (technique name)
I must admit that I solved this task at the very end, despite the obvious answer. The issue was that I focused on searching for the correct MITRE technique. Why did I do this? Simply because in most challenges, they ask for a MITRE technique, and I had grown accustomed to it. So, for future reference, I need to read the task description more carefully :). The obvious answer to this question is typosquatting, as the attacker omitted one letter in the name, i.e., instead of PublishIgnore, they created a package called PublishIgnor, omitting the e.
Answer: typosquatting
Task 7
Determine the full path of the file within the package containing the malicious code.
During the solution to the first task, I came across the .nugget directory. It was here that the malicious package downloaded by the user was located. Upon reviewing its contents, I found the init.ps1 script. The script, after disabling protections, would proceed to download another part of the malicious software, uninstall.exe (Fig. 7).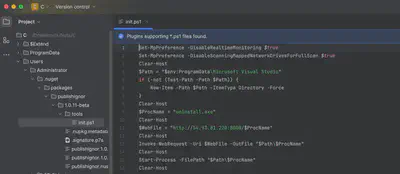
Answer: C:\Users\Administrator\.nuget\packages\publishignor\1.0.11-beta\tools\init.ps1
Task 8
When tampering with the system’s security settings, what command did the attacker employ?
The answer to this question was found while solving previous tasks. In the first line of the script, the attacker disables real-time monitoring (Fig. 7).
Answer: Set-MpPreference -DisableRealtimeMonitoring $true
Task 9
Following the security settings alteration, the attacker downloaded a malicious file to ensure continued access to the system. Provide the SHA1 hash of this file.
Analyzing the script, I first checked the contents of the C:\ProgramData\Microsoft Visual Studio directory. However, the task creators didn’t provide any files in that directory. So, I decided to try my luck by checking the provided Windows Defender logs. In the Windows Defender logs, I found information about the detected malware and its SHA1 hash (Fig. 8).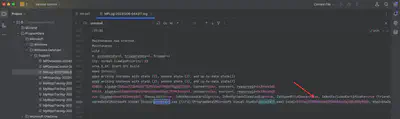
Answer: 57b7acf278968eaa53920603c62afd8b305f98bb
Task 10
Identify the framework utilized by the malicious file for command and control communication.
In the same logs, I also found the framework used for communication by the malware (Fig. 9).
Answer: sliver
Task 11
At what precise moment was the malicious file executed?
In the C:\Windows\Prefetch directory, I found the prefetch file associated with the execution of the malware. After running the command PECmd.exe -f UNINSTALL.EXE-07032A62.pf, I found the answer to the question (Fig. 10).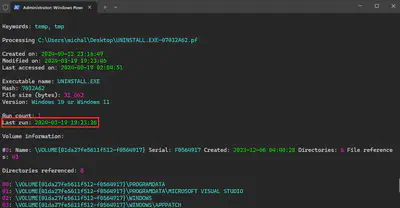
Answer: 2024-03-19 19:23:36
Task 12
The attacker made a mistake and didn’t stop all the features of the security measures on the machine. When was the malicious file detected? Provide the timestamp in UTC.
The answer was obtained during the completion of tasks 9 and 10 from the Windows Defender logs (Fig. 8).
Answer: 2024-03-19 19:33:32
Task 13
After establishing a connection with the C2 server, what was the first action taken by the attacker to enumerate the environment? Provide the name of the process.
The first command attackers usually execute is whoami on the system. To confirm this, I checked the contents of the Prefetch directory. Indeed, such a program was executed (Fig. 11).
Answer: whoami.exe
Task 14
To ensure continued access to the compromised machine, the attacker created a scheduled task. What is the name of the created task?
In the directory C:\Windows\System32\Tasks, all tasks added to the machine are located. Using the command
find . -type f -exec cat {} \;, I listed the contents of all tasks and then searched for the task containing the creation date corresponding to the time the attacker gained access to the machine (Fig. 12).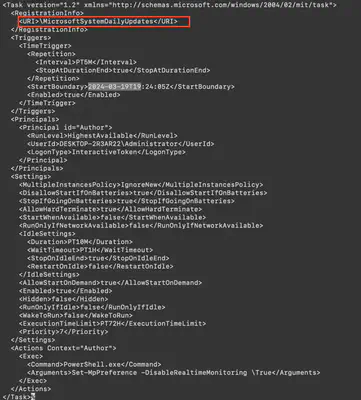
Answer: MicrosoftSystemDailyUpdates
Task 15
When was the scheduled task created? Provide the timestamp in UTC.
From the solution to the previous task.
Answer: 2024-03-19 19:24:05
Task 16
Upon concluding the intrusion, the attacker left behind a specific file on the compromised host. What is the name of this file?
I spent quite some time searching for the answer to this question. Although I noticed the unusual file Updater.exe in the C:\ProgramData directory, it was clearly malware but didn’t contain information about the previous name. Additionally, VirusTotal didn’t provide such information either. Finally, I focused on the prefetch files, hoping the attacker first executed the file under its old name. And that turned out to be the case – while analyzing the prefetch files, I found an unusual file name file.exe (Fig. 13).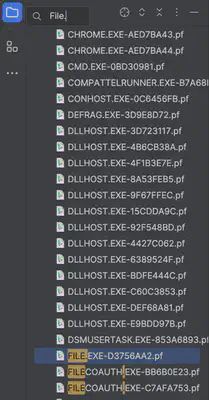
Answer: file.exe
Task 17
As an anti-forensics measure. The threat actor changed the file name after executing it. What is the new file name?
While solving previous tasks, I noticed the file Updater.exe in the ProgramData directory. This file shouldn’t be there; it’s an unusual file. After investigating it using VirusTotal, I confirmed my suspicion that it was a malicious file (Fig. 14).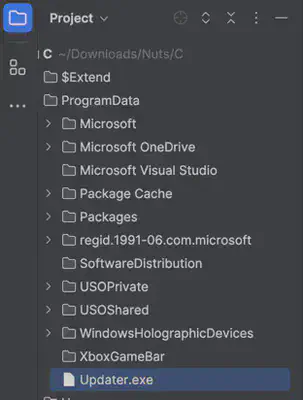
Answer: Updater.exe
Task 18
Identify the malware family associated with the file mentioned in the previous question (17).
Through trial and error with VirusTotal, I eventually identified the malware family (Fig. 15).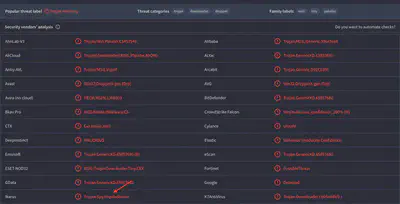
Answer: Impala
Task 19
When was the file dropped onto the system? Provide the timestamp in UTC.
Using MFTExplorer, I retrieved the file creation time in the system (Fig. 16).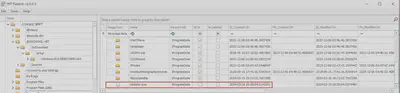
Answer: 2024-03-19 19:30:04