HTB Sherlock - Nubilum-1 Writeup
 HTB Sherlock - Nubilum-1 Writeup
HTB Sherlock - Nubilum-1 WriteupSherlock Scenario
Our cloud administration team recently received a warning from Amazon that an EC2 instance deployed in our cloud environment is being utilised for malicious purposes. Our sysadmin team have no recollection of deploying this EC2, however do recall logging onto the AWS console and finding in excess of 6 EC2s running, which he did not recall deploying. You have been provided with the interview with our Cloud sysadmin within the triage.
Artefacts
After extracting the downloaded ZIP file, the following files and directories are available to solve the task (Fig. 1):
CloudTrail- directory containing AWS logs,catscale_ip-172-31-24-20-20230130-1628.tar.gz- artefacts collected from the compromised machine using the Catscale tool,forela-storage- a copy of files from the S3 bucket,interview.txt- a transcript of the interview with the administrator,unusual-directory.zip- a directory found on the compromised machine.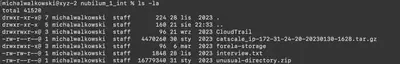
Fig. 1. Contents of the extracted ZIP file.
Solution
Task 1
Which AWS IAM account was compromised by the TA?
First, using the command find . -type f -name "*.json" -exec cat {} \; > all.json, I merged all the log files into a single file. Then I spent quite a bit of time searching for the correct answer without success. I started by extracting user agents and found the value “kali” in one of them, then searched for the associated IP address. Later, I thought of approaching the task in a different, more CTF-oriented way. Since the expected flag format was ******-***-*********n (Fig. 2), I decided to use regex to find the answer. I used the command cat all.json | jq | grep -E "[a-zA-Z0-9]{6}-[a-zA-Z0-9]{3}-[a-zA-Z0-9]{9}n" | grep userName | uniq, which took some time, but I eventually found only one AWS IAM account value that matched the pattern (Fig. 3).
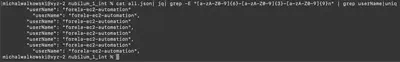
Answer: forela-ec2-automation
Task 2
Where did the attacker locate the hard-coded IAM credentials?
I started by reviewing the contents of the forela-storage directory. The file ec2.py caught my attention (Fig. 4).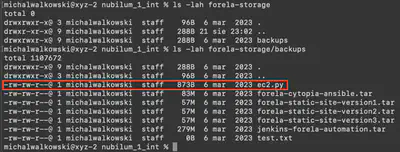
forela-storage directory.
cat forela-storage/backups/ec2.py file.jq '.Records | .[] | select(.userIdentity.accountId== "anonymous") | select(.eventName=="GetObject") | select(.errorCode!="AccessDenied") | select(.errorCode!="NoSuchKey")' all.json, I listed all successful file downloads by the anonymous user. I then checked whether the previously identified file ec2.py was in the logs. Among the listed events, the file ec2.py appeared only once. This not only helped me confirm the exact path but also identify the download time, which allowed me to narrow down my further investigations.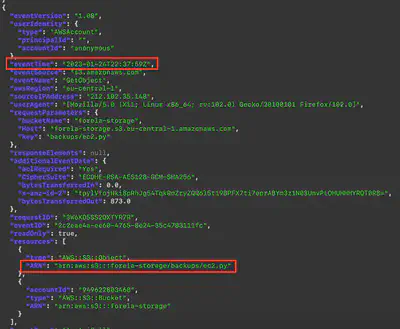
Answer: /backups/ec2.py
Task 3
In total, how many EC2 hosts were deployed by the TA?
The next step was to extract all actions performed by the compromised account after the attacker gained access. I selected the file download time of ec2.py as the reference point. Using the command jq '.Records[] | select(.userIdentity.userName == "forela-ec2-automation" and .eventTime >= "2023-01-24T22:37:59Z")' all.json > compromised.json, I extracted all events. I then focused on events related to instance creation. There were 8 events responsible for creating 13 EC2 instances (Fig. 7).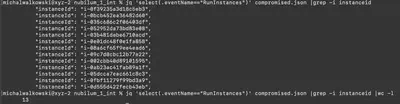
Answer: 13
Task 4
What is the name of the key pair/s generated by the attacker?
Using the command jq 'select(.eventName=="CreateKeyPair")' compromised.json, I listed the events related to key creation in AWS (Fig. 8).
Answer: 1337.key, 13337
Task 5
What time were the key pair/s generated by the attacker?
From the previous task (Fig. 9).
Answer: 2023-01-24T22:48:34Z,2023-01-25T12:01:38Z
Task 6
What are the key pair ID/s of the key/s generated by the attacker?
From Task 4 (Fig. 10).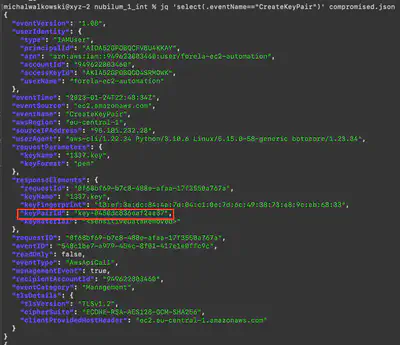
Answer: key-0450dc836eaf2aa37
Task 7
What is the description of the security group created by the attacker?
Using the command jq 'select(.eventName=="CreateSecurityGroup")' compromised.json, I found one event related to the creation of a security group. The answer was found in the groupDescription field (Fig. 11).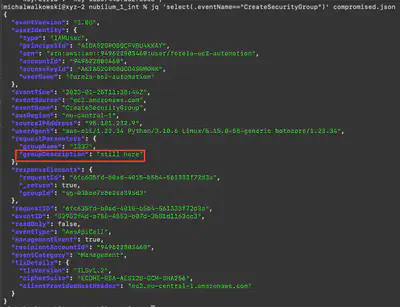
Answer: still here
Task 8
At what time did the Sys Admin terminate the first set of EC2s deployed?
To answer this question, I had to return to the originally created file all.json. Considering the time when the attacker obtained the login credentials, I used the command jq '.Records[] | select(.eventName=="TerminateInstances" and .eventTime >= "2023-01-24T22:37:59Z") | {time: .eventTime}' all.json and found two results (Fig. 12).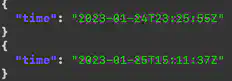
Answer: 2023-01-24 23:25
Task 9
Can we confirm the IP addresses used by the TA to abuse the leaked credentials? (Ascending Order)
Having already extracted the file with events performed using the compromised IAM account, I used the command cat compromised.json | grep sourceIPAddress | sort | uniq to extract the unique IP addresses used by the attacker (Fig. 13).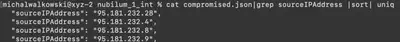
Answer: 95.181.232.4, 95.181.232.8, 95.181.232.9, 95.181.232.28
Task 10
In addition to the CloudTrail data and S3 access, we have provided artefacts from the endpoint reported by AWS. What is the name of the malicious application installed on the EC2 instance?
After extracting the archive unusual-directory.zip, I received a new directory poshc2. Poshc2 is a C2 framework (Fig. 14).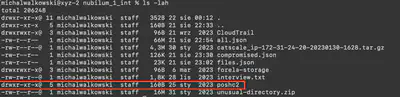
unusual-directory.zip.
Answer: PoshC2
Task 11
Please provide the hostname and username details of any victims of the C2 server.
In the directory poshc2/money/, I found the file poshc2_server.log, which contained information from the running PoshC2 instance. Upon reviewing it, I found the hostname and username (Fig. 15).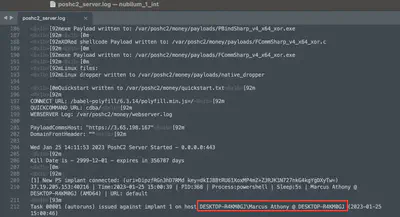
Answer: DESKTOP-R4KM0GJ\Marcus Athony