HTB Sherlock - Knock Knock Writeup
 HTB Sherlock - Knock Knock Writeup
HTB Sherlock - Knock Knock WriteupSherlock Scenario
A critical Forela Dev server was targeted by a threat group. The Dev server was accidentally left open to the internet which it was not supposed to be. The senior dev Abdullah told the IT team that the server was fully hardened and it’s still difficult to comprehend how the attack took place and how the attacker got access in the first place. Forela recently started its business expansion in Pakistan and Abdullah was the one IN charge of all infrastructure deployment and management. The Security Team need to contain and remediate the threat as soon as possible as any more damage can be devastating for the company, especially at the crucial stage of expanding in other region. Thankfully a packet capture tool was running in the subnet which was set up a few months ago. A packet capture is provided to you around the time of the incident (1-2) days margin because we don’t know exactly when the attacker gained access. As our forensics analyst, you have been provided the packet capture to assess how the attacker gained access. Warning : This Sherlock will require an element of OSINT to complete fully.
Artefacts
To solve the task, we received a file named Capture.pcap, which is a network traffic capture. The file covers traffic from one day, 2 hours, 40 minutes, and 12 seconds, from 2023-03-20 15:37:35 to 2023-03-21 18:17:48, and contains 293 921 packets (Fig. 1).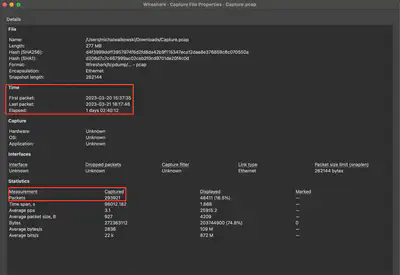
Capture.pcap file.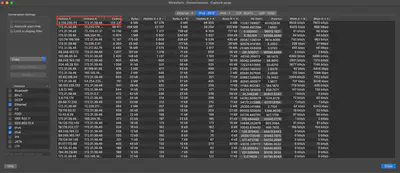
Solution
Task 1
Which ports did the attacker find open during their enumeration phase?
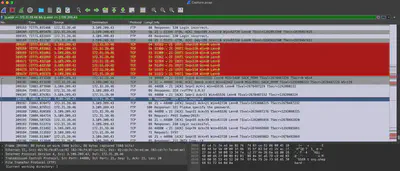
Reviewing further network traffic, I noticed that right after the ICMP packets sent by the attacker, there is an attempt to scan ports 21, 22, 80, 443, 3306, 6379, and 8086. For ports 21, 22, 3306, 6379, and 8086, the full TCP SYN procedure takes place, as described in a previous article during the resolution of Aptnightmare (Fig. 4).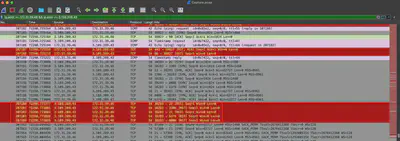
Answer: 21,22,3306,6379,8086
Task 2
Whats the UTC time when attacker started their attack against the server?
I went back to the beginning of the communication between the server and the attacker and selected the first packet, which was timestamped 21/03/2023 10:42:23 (Fig. 5).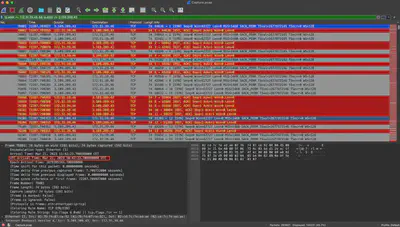
Answer: 21/03/2023 10:42:23
Task 3
What’s the MITRE Technique ID of the technique attacker used to get initial access?
After filtering the traffic for TCP port 21, it can be observed that the attacker uses a list of predefined users during the access attempt (Fig. 6), which suggests that they likely obtained such a list from somewhere.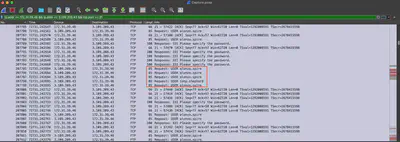
Answer: T1110.003
Task 4
What are valid set of credentials used to get initial foothold?
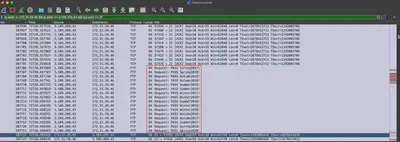
Reviewing the traffic for port 21, I found two Login successful responses from the server. In both cases, after selecting the follow the stream option, I receive the answer to this question. In Fig. 8, I decided to present the second found answer because only after selecting it in the follow the stream option do we have access to the entire communication of the attacker after logging into the FTP server (Fig. 9).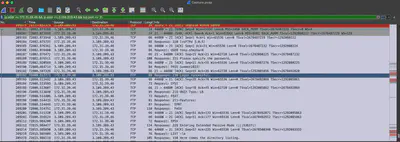
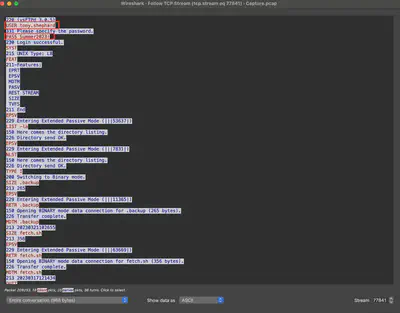
Answer: tony.shephard:Summer2023!
Task 5
What is the Malicious IP address utilized by the attacker for initial access?
I obtained the answer to this question during the initial analysis of the Capture.pcap file. During the analysis, I identified the attacker’s IP address as 3.109.209.43.
Answer: 3.109.209.43
Task 6
What is name of the file which contained some config data and credentials?
In the communication, I found information that the attacker downloaded two files from the FTP server: .backup and fetch.sh (Fig. 10).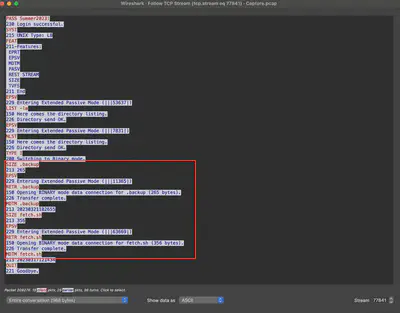
fetch.sh file, we see that a connection to the database is established and a SELECT query is executed, which looks like regular data retrieval or a health check. The .backup file, on the other hand, appears to be a configuration file. After a short search, I found that it is a configuration file for knockd.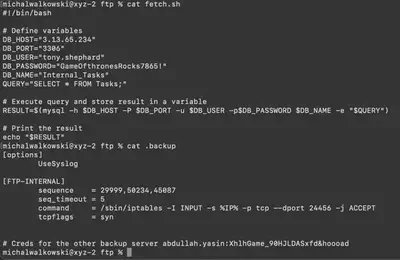
Answer: .backup
Task 7
Which port was the critical service running?
From the configuration file .backup, we see the iptables command with a redirection to port 24456 (Fig. 12).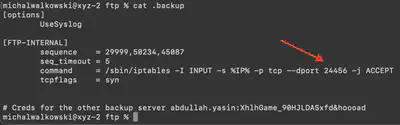
Answer: 24456
Task 8
Whats the name of technique used to get to that critical service?
I found the answer to this question while identifying the configuration file .backup (Fig. 12).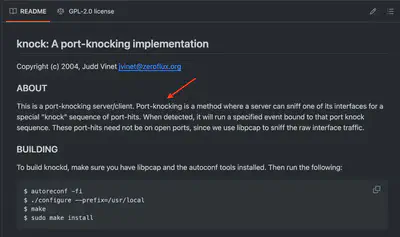
Answer: Port Knocking
Task 9
Which ports were required to interact with to reach the critical service?
From the configuration file .backup (Fig. 14).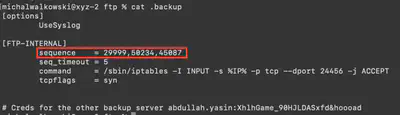
Answer: 29999,45087,50234
Task 10
Whats the UTC time when interaction with previous question ports ended?
Checking the time of the last sent packet for each port, I got the answer: 21/03/2023 10:58:50 (Fig. 15).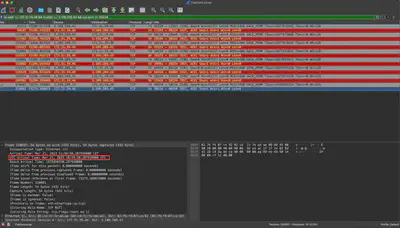
Answer: 21/03/2023 10:58:50
Task 11
What are set of valid credentials for the critical service?
Analyzing the pcap file, I found communication between the attacker and the server on port 24456. After checking the contents of the packets, I noticed that it was FTP communication (Fig. 16).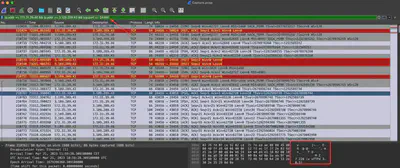
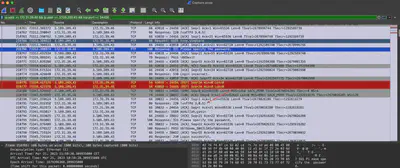
Answer: abdullah.yasin:XhlhGame_90HJLDASxfd&hoooad
Task 12
At what UTC Time attacker got access to the critical server?
After selecting the packet in which the server informs the client of a successful login to the service, I obtained the answer to the question (Fig. 19).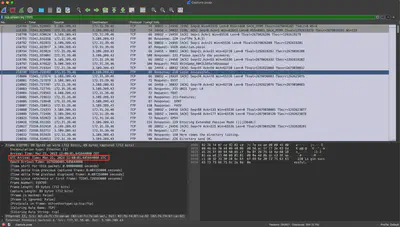
Answer: 21/03/2023 11:00:01
Task 13
Whats the AWS AccountID and Password for the developer “Abdullah”?
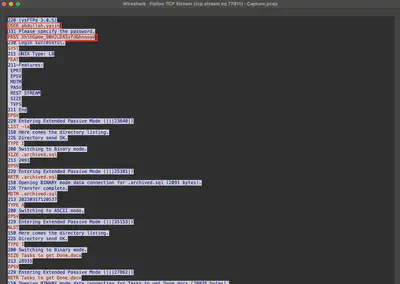
After reviewing the communication conducted by the attacker, it can be seen that several files were downloaded using the FTP protocol (Fig. 20).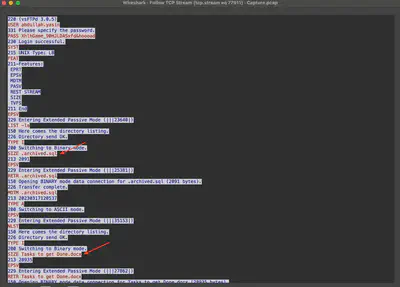
.backup and fetch.sh (Fig. 21). Since the number of files slightly increased, I decided to export all of them.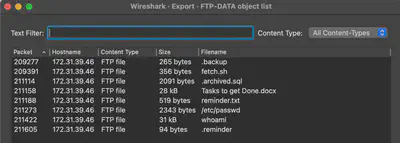
.archived.sql file, which is a dump of the MySQL database (Fig. 22).
Answer: 391629733297:yiobkod0986Y[adij@IKBDS
Task 14
Whats the deadline for hiring developers for forela?
Reviewing the exported files, I found the answer to the question in the Tasks to get Done.docx file (Fig. 23).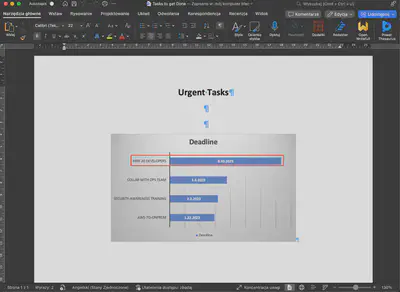
Answer: 30/08/2023
Task 15
When did CEO of forela was scheduled to arrive in pakistan?
Reviewing the exported files, I found the answer to the question in the reminder.txt file (Fig. 24).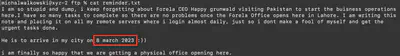
Answer: 08/03/2023
Task 16
The attacker was able to perform directory traversel and escape the chroot jail. This caused attacker to roam around the filesystem just like a normal user would. Whats the username of an account other than root having /bin/bash set as default shell?
Reviewing the exported files, I found the answer to the question in the passwd file (Fig. 25).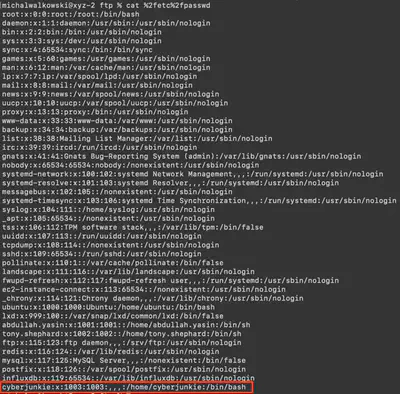
Answer: cyberjunkie
Task 17
Whats the full path of the file which lead to ssh access of the server by attacker?
Analyzing the FTP communication, I noticed that the attacker navigates the file system using the CWD command and moves to the /opt/reminders directory. Then, from this directory, they download the .reminder file (Fig. 26).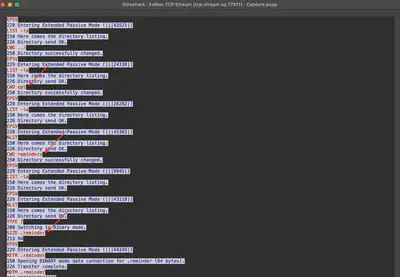
Answer: /opt/reminders/.reminder
Task 18
Whats the SSH password which attacker used to access the server and get full access?
The contents of the .reminder file indicate that the attacker found a password in a Git repository (Fig. 27).
site:github.com Forela into Google. As a result, I received a link to the Forela Finance repository (Fig. 28).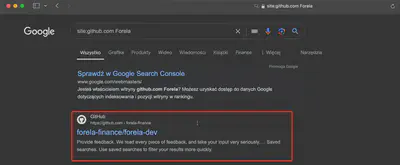
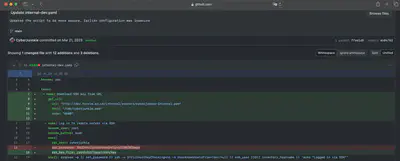
Answer: YHUIhnollouhdnoamjndlyvbl398782bapd
Task 19
Whats the full url from where attacker downloaded ransomware?
The task description indicates that the attacker downloaded ransomware as a file. Initially, I checked if there was any clue in the available files for export. For this, I chose “Export Objects -> HTTP Stream” and then changed the Content-Type filter. After selecting the application/zip option (Fig. 31, arrow 1), to my satisfaction, only one file appeared on the list, which was named Ransomware2_server.zip (Fig. 31, arrow 2). After selecting the file, I was immediately redirected to the packet in Wireshark corresponding to the beginning of the ZIP file transfer (Fig. 31, arrow 3).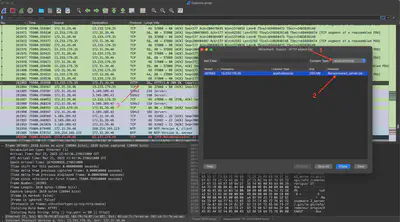
follow the stream, we obtain the request sent to download the file (Fig. 32).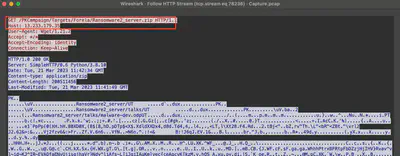
Answer: http://13.233.179.35/PKCampaign/Targets/Forela/Ransomware2_Server.zip
Task 20
Whats the tool/util name and version which attacker used to download ransomware?
From the previous task, in the follow the stream, the user-agent header is available (Fig. 32).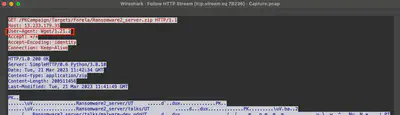
Answer: Wget/1.21.2
Task 21
Whats the ransomware name?
After exporting the ZIP file during task 18, I unpacked it and then found the solution to the task in the src directory. The name immediately caught my attention as it was similar to another once-popular ransomware, which is still the subject of many articles – WannaCry (Fig. 33).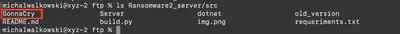
Answer: GonnaCry