HTB Sherlock - Jugglin Writeup
 HTB Sherlock - Heartbreaker Writeup
HTB Sherlock - Heartbreaker WriteupSherlock Scenario
Forela Corporation heavily depends on the utilisation of the Windows Subsystem for Linux (WSL), and currently, threat actors are leveraging this feature, taking advantage of its elusive nature that makes it difficult for defenders to detect. In response, the red team at Forela has executed a range of commands using WSL2 and shared API logs for analysis.
Artefacts
To solve the task, we have two files: Attacker.apmx64 and Insider.apmx64 (Fig 1).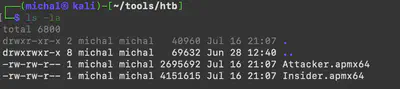
Honestly, this is my first encounter with such an extension. Therefore, I first used the file command to gather information about the received files. As a result of the command, I learned that they are zip files (Fig 2).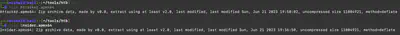
file command.
Before unpacking them, I decided to consult Google. Already in the first search result, I found the answer to my question. It turned out that the files can be opened using the API Monitor software (Fig 3).
I downloaded the software from this site and checked if the files worked (Fig 4). However, before proceeding with solving the task, I took a moment to learn what API Monitor is and what it is used for. From the manufacturer’s website, I learned that API Monitor is free software that allows monitoring and controlling API calls made by applications and services. It is a powerful tool that enables checking the operation of applications and services or tracking issues occurring in your own applications.
Sounds interesting.
As it turned out in the further parts, the tasks to be solved are very simple, and you just need to look for the appropriate API calls. There is no need to decode anything, everything is provided in plaintext, though sometimes you need to look from a “wider” perspective 😊
Solution
Task 1
What was the initial command executed by the insider?
After opening the file, I had to spend some time working with the application to understand how to navigate it. Additionally, based on recommendations found online, it is always advisable to start the analysis with an exe file. While analyzing the file, I noticed that the first command executed by the insider is captured character by character (Fig 5).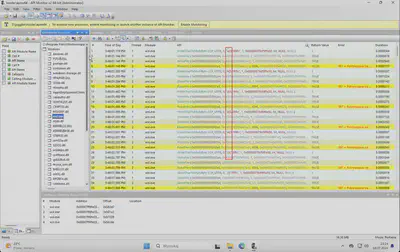
Answer: whoami
Task 2
Which string function can be intercepted to monitor keystrokes by an insider?
To solve this task, I examined the functions being called. First, the WideCharToMultiByte function from wsl.exe is called, and then the parameter is passed to the RtlUnicodeToUTF8N function from KERNELBASE.dll (Fig 6).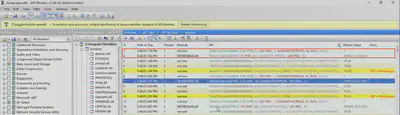
Answer: RtlUnicodeToUTF8N, WideCharToMultiByte
Task 3
Which Linux distribution the insider was interacting with?
A few calls later, I found the result of the whoami command, which returns the username kali (Fig 7). Since the username is quite specific, I immediately assumed it only appears on one operating system, which is Kali.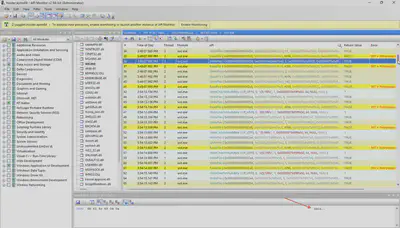
whoami command.
Answer: kali
Task 4
Which file did the insider access in order to read its contents?
In the same way that I detected the first command executed by the insider (whoami), a few calls later, I found information about the execution of the cat flag.txt command (Fig 8).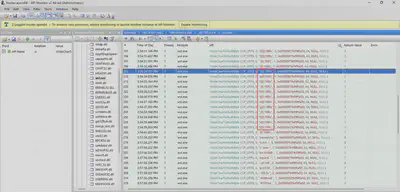
Answer: flag.txt
Task 5
Submit the first flag.
Just like in the previous case, a few calls later, there is the result of the cat flag.txt command, where I found the first flag (Fig 9).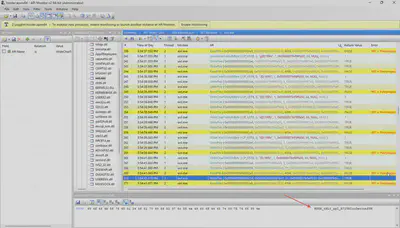
Answer: HOOK_tH1$_apI_R7lUNIcoDet0utf8N
Task 6
Which PowerShell module did the insider utilize to extract data from their machine?
Reviewing the subsequent API calls, I noticed that the insider runs PowerShell with the Invoke-WebRequest module (Fig 10).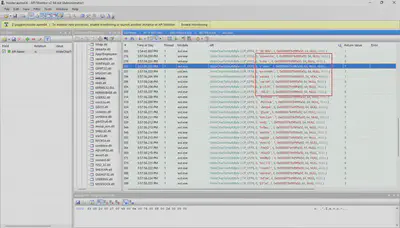
Answer: Invoke-WebRequest
Task 7
Which string function can be intercepted to monitor the usage of Windows tools via WSL by an insider?
Studying the API calls, I noticed that the PowerShell invocation by the insider was passed to the KERNELBASE.dll module to the RtlUTF8ToUnicodeN function, which simultaneously provided the answer to the question (Fig 11).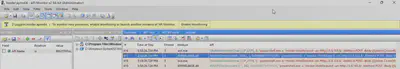
Answer: RtlUTF8ToUnicodeN
Task 8
The insider has also accessed ‘confidential.txt’. Please provide the second flag for submission.
The second flag is also found a bit further down after the execution of the powershell.exe command (Fig 12).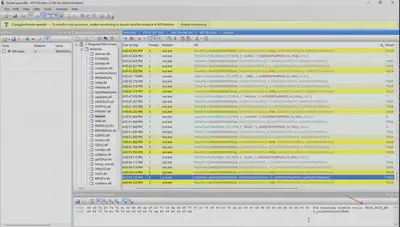
Answer: H0ok_ThIS_@PI_rtlutf8TounICOD3N
Task 9
Which command executed by the attacker resulted in a ’not found’ response?
To solve the next tasks, I now proceed to analyze the Attacker.apmx64 file. In the 26th API call, I find the answer to the question (Fig 13).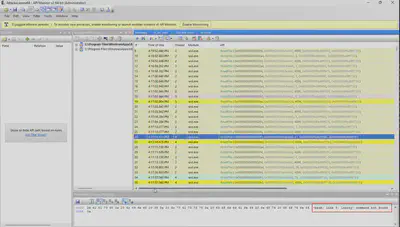
lsassy
Task 10
Which link was utilized to download the ’lsassy’ binary?
In the 32nd API call, I noticed the execution of the wget command and the URL from which the attacker downloaded the lsassy software (Fig 14).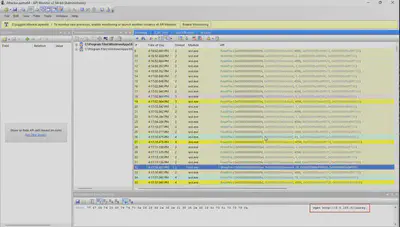
Answer: http://3.6.165.8/lsassy
Task 11
What is the SHA1 hash of victim ‘user’?
I must admit, it took me a while. It turned out that the user’s hash was almost at the very end of the list of API calls (Fig 15).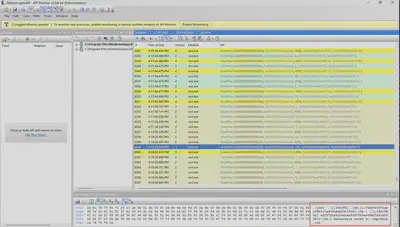
Answer: e8f97fba9104d1ea5047948e6dfb67facd9f5b73
Task 12
When an attacker utilizes WSL2, which WIN32 API would you intercept to monitor its behavior?
If we review the previous task solutions, we will notice that almost all the answers are related to the execution of the WriteFile function. And that was the correct answer as well. :)
Answer: WriteFile