HTB Sherlock - Jinkies Writeup
 HTB Sherlock - Jinkies Writeup
HTB Sherlock - Jinkies WriteupSherlock Scenario
You’re a third-party IR consultant and your manager has just forwarded you a case from a small-sized startup named cloud-guru-management ltd. They’re currently building out a product with their team of developers, but the CEO has received word of mouth communications that their Intellectual Property has been stolen and is in use elsewhere. The user in question says she may have accidentally shared her Documents folder and they have stated they think the attack happened on the 6th of October. The user also states she was away from her computer on this day. There is not a great deal more information from the company besides this. An investigation was initiated into the root cause of this potential theft from Cloud-guru; however, the team has failed to discover the cause of the leak. They have gathered some preliminary evidence for you to go via a KAPE triage. It’s up to you to discover the story of how this all came to be. Warning: This sherlock requires an element of OSINT and players will need to interact with 3rd party services on internet.
Artefacts
After extracting the downloaded zip file, we have two directories: LiveResponse and TriageData, containing a total of 3104 files (Fig 1).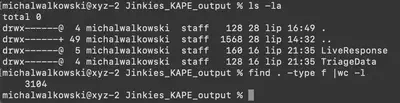
The LiveResponse directory contains logs, including process dumps, open ports, and a copy of the system registry (Fig 2).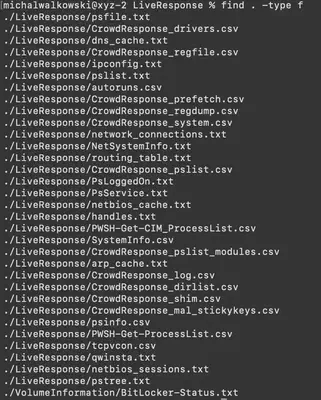
LiveResponse directory.
The TriageData directory contains a copy of files from the compromised system (Fig 3).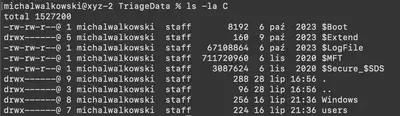
TriageData directory.
Solution
Task 1
Which folders were shared on the host? (Please give your answer comma separated, like this: c:\program files\share1, D:\folder\share2)
After reviewing the files provided for the task, I determined that the operating system is Windows. In Windows, the settings for shared directories are located in the registry under the key HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Shares. By executing the command grep -Fir "HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Shares" in the LiveResponse directory, I found several registry entries and information about the values I should look for (Fig. 4). Adding another grep command, I obtained a list of all shared resources, which are: C:\Users and C:\Users\Velma\Documents (Fig. 5).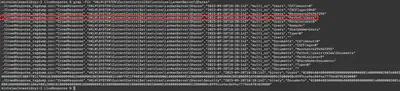
grep -Fir 'HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Shares'.
Answer: C:\Users\Velma\Documents, C:\Users
Task 2
What was the file that gave the attacker access to the users account?
The search using the chainsaw tool yielded no results, so I returned to browsing the directories. It was obvious to me that the attacker had downloaded a file from the home directory of the user Velma. An interesting directory was her project located in C/users/Velma/Documents/Python Scripts + things, so I started my search there. The simplest methods are always the best. After executing the command grep -r password ., the first file on the list caught my attention (Fig. 6). It turned out to be an IBD file, a MySQL table created by the InnoDB database engine.
Reading the contents of the file confirmed my finding—it was an important file containing user passwords and email addresses (Fig. 7).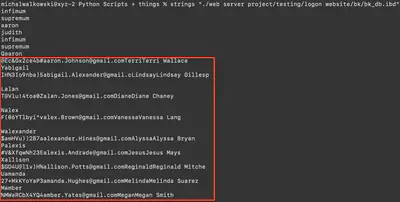
bk_db.ibd file.
Answer: bk_db.ibd
Task 3
How many user credentials were found in the file?
Using the command strings "./web server project/testing/logon website/bk/bk_db.ibd" | grep @ | wc -l, I counted all occurrences of email addresses, which was equivalent to the number of passwords contained in the file (Fig. 8).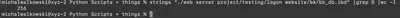
bk_db.ibd file.
Answer: 216
Task 4
What is the NT hash of the users password?
In the available files, I noticed that I have a SAM file. Extracting password hashes from the SAM database is possible using the secretsdump script from the impacket package. Using the command impacket-secretsdump -sam TriageData/C/Windows/system32/config/SAM -system TriageData/C/Windows/system32/config/SYSTEM LOCAL, I displayed all the hashes. For the user Velma, the NT hash is 967452709ae89eaeef4e2c951c3882ce (Fig. 9).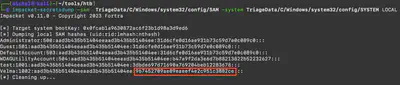
Answer: 967452709ae89eaeef4e2c951c3882ce
Task 5
Does this password match that found in the previous file? (Yes or No)
I returned to the bk_db.ibd file and used the command strings "./web server project/testing/logon website/bk/bk_db.ibd" | grep -i Velma to search for the user’s password. It turned out to be peakTwins2023fc (Fig. 10).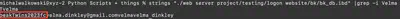
bk_db.ibd file.
Next, using CyberChef, I calculated the NT hash of the password (Fig. 11). As you can see, it is the same password.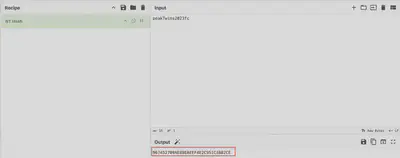
Answer: Yes
Task 6
What was the time the attacker first interactively logged on to our users host?
After obtaining the login and password, the attacker remotely logged into the machine using the RDP protocol. Therefore, I looked for event number 4624. The logon type I’m interested in is 3, which indicates a successful network logon by a user. Using the command chainsaw search -t 'Event.System.EventID: =4624' -t 'Event.EventData.LogonType: =3' ../htb/TriageData/C/Windows/system32/winevt/ --skip-errors, I received three results. The last result turned out to be correct (Fig. 12).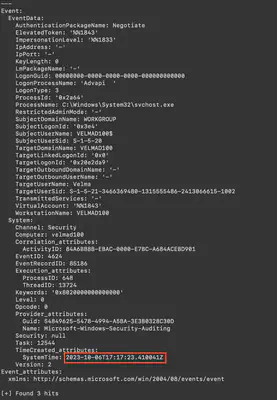
Answer: 2023-10-06 17:17:23
Task 7
What’s the first command the attacker issues into the Command Line?
Using the command chainsaw search --timestamp 'Event.System.TimeCreated_attributes.SystemTime' --from "2023-10-06T17:17:23" --skip-errors "cmd.exe" ../htb/TriageData/C/Windows/system32/winevt/, I searched for all events that contained cmd.exe and occurred after the attacker successfully logged in. The second event on the list revealed the command executed by the attacker (Fig. 13).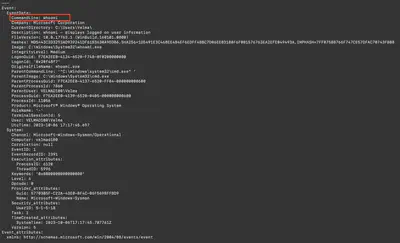
Answer: whoami
Task 8
What is the name of the file that the attacker steals?
Searching through the list of commands executed after 2023-10-06T17:17:23, the only file the attacker referenced was Version-1.0.1 - TERMINAL LOGIN.py (Fig. 14). The attacker opened it in an editor. Considering the content of the next task, the file transfer was likely done using a browser and the copy-paste method.
Answer: Version-1.0.1 - TERMINAL LOGIN.py
Task 9
What’s the domain name of the location the attacker ex-filtrated the file to?
The attacker used the user’s browser for data transfer. Therefore, I immediately started searching the browser history. In the file TriageData/C/Users/Velma/AppData/Local/Google/Chrome/User Data/Default/History, in the url table, I noticed the following entries (Fig. 15). It appears that the attacker uploaded the file to pastes.io.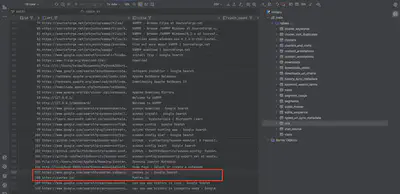
Answer: pastes.io
Task 10
What is the handle of the attacker?
From the task description, I learned that the attacker must have left a file on the system containing their signature. Earlier, I noticed that the artifacts included a MFT (Master File Table) dump. I decided that this would be a good starting point for the search. Therefore, I first executed the command MFTECMD.exe -f "$MFT" --csv . --csvf mft.csv to convert the entry into event format. Then, I opened the mft.csv file in TimeLine Explorer. For the file search, I made the following assumptions: the file must have been created after the attacker logged into the machine, it is likely a .txt text file, and it must be located somewhere visible in the user Velma’s home directory. Additionally, to be readable, the file must be smaller than 600 bytes. The first file that met these criteria was learn.txt located in C:\Users\Velma\Pictures\ (Fig. 16).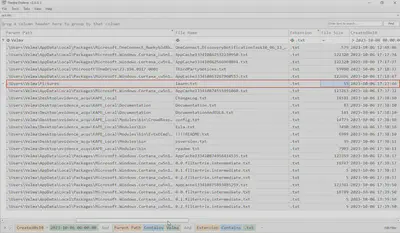
I decided to check its contents using the MFT Explorer software. It was a bullseye. The file content, lol check your drivers next time idiot, signed pwnmaster12, clearly indicated that this file was created by the attacker (Fig. 17).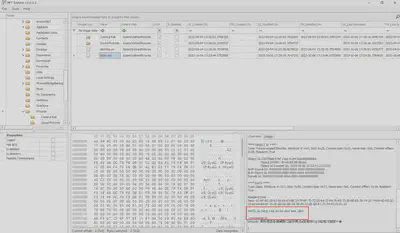
Answer: pwnmaster12