HTB Sherlock - Heist Writeup
 HTB Sherlock - Heist Writeup
HTB Sherlock - Heist WriteupSherlock Scenario
Forela recently received complaints from viewers that the live stream on their YouTube channel was showing strange content. Instead of the usual company content, the live stream showed videos promoting cryptocurrency scams. The channel was used to showcase the company’s products and services and provide educational content related to the industry they were in. Alonzo Spire, the IT administrator of Forela, managed the YouTube channel. The incident response team was notified of an incident as soon as complaints were received. Alonzo’s system was triaged, and artifacts were acquired from his system for forensic analysis to confirm how the company’s channel got hacked.
Artefacts
To solve the task, we received the following files:
Email.eml- an email received by the user,Heist.pcap- a communication capture,Kape_Acquisition.zip- a partial copy of the C drive. After unpacking theKape_Acquisition.zipfile, we have a total of 917 files at our disposal (Fig. 1).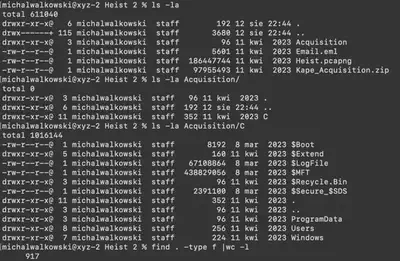
Fig 1. Retrieved artifacts.
Solution
Task 1
At what time was the suspected phishing email received in the victim’s inbox? (UTC)
In the main directory of the task, there is a file named Email.eml. After reading its content, I noticed that it is a copy of an email containing phishing. The Received field contains the information I was looking for (Fig 2).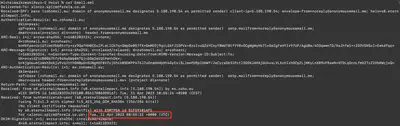
Answer: 2023-04-11 08:55:22
Task 2
Please provide the download URL that was utilized to retrieve the file initially downloaded as part of this security event.
Since the user downloaded the malicious attachment, they likely did so using the system’s default browser. I found that the user had two browsers installed: Edge and Chrome. I assumed that since Chrome was installed, it was their primary browser. In the History file, in the downloads table, I found the name of the downloaded malicious file and the ID needed for further investigation (Fig 3).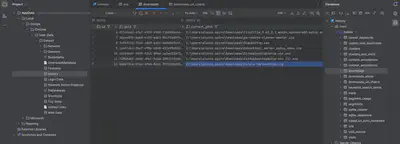
download_url_chains table, I discovered three entries. This means the user was redirected twice before downloading the malicious attachment. The last entry is the URL from which the malicious attachment was downloaded (Fig 4).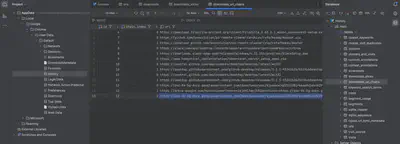
Answer: https://doc-0s-5g-docs.googleusercontent.com/docs/securesc/sjpaukai4p255id8irbsaa0d1ds9k29c/o8kmueker1h57tkoe14o1osgi4uhbafl/1681208325000/03105725814018983462/13809461445078444789Z/1KsmFJYLzRefViXzeyWYOoojfewRmJgpp?e=download&uuid=d3c34b3f-c99f-42b3-84b3-dfc4ac4f609a&nonce=iojdml3dsj58i&user=13809461445078444789Z&hash=o5gmgdrljfhdo4hvrt3oparan4sq0hm5
Task 3
What is the name of the file suspected to have been initially downloaded as part of this security event?
The name of the malicious attachment downloaded from the previous task (Fig 3).
Answer: Forela-Partnership.zip
Task 4
When was this file downloaded onto the system?
In the downloads table, in the same row where the name of the file is located, in the last_visit_time column, which indicates the last visit time of the user to a particular URL, I found the value 13325681964931025. This is a timestamp recorded in the WebKit/Chrome format. Using the epochconverter tool, I converted this timestamp to a standard format and obtained the answer.
Answer: 2023-04-11 10:19:24
Task 5
What is the name of the file that initiated malicious activity on the endpoint?
Using the command MFTECMD.exe -f "$MFT" --csv ". ---csvf mft.csv", I processed the MFT file into CSV format, and then used Timeline Explorer for further analysis. Knowing the download time of the malicious software and the path where it was downloaded, I found the answer (Fig 6).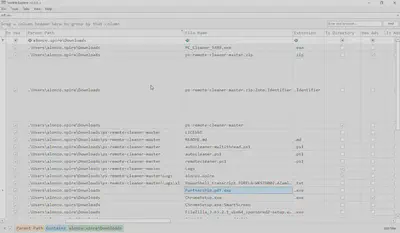
Answer: Partnership.pdf.exe
Task 6
What file type was the malicious payload disguised as to deceive the user into executing it?
Based on the detected name of the malicious software, it can be inferred that the attacker tried to disguise it as a PDF file.
Answer: pdf
Task 7
From which directory path was the malicious file executed?
To solve this task, we received Prefetch files containing information about the applications and services executed on the victim’s operating system. Among them, I found a file named PARTNERSHIP.PDF.EXE-CCA24020.pf, which corresponds to the previously detected name of the malicious software. Using the command PECmd.exe -f C\Windows\prefetch\PARTNERSHIP.PDF.EXE-CCA24020.pf, I obtained the path from which the malicious software was executed (Fig 7).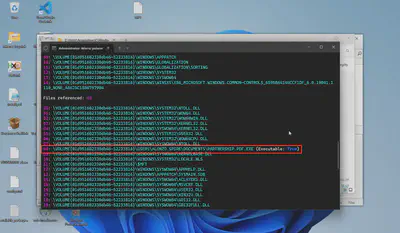
Answer: C:\USERS\ALONZO.SPIRE\DOCUMENTS\
Task 8
There was a file on the user’s desktop with a note. What were the contents of the note?
Using MFTExplorer, I found the user’s home directory and desktop. On the desktop, there was only one file containing a note named reminder.txt (Fig 8).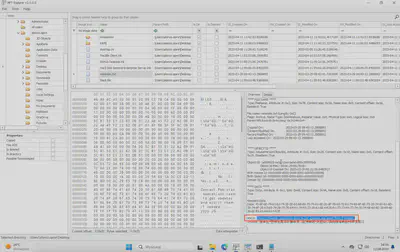
Answer: Contact Pakistan operations team to get updates and assist them if needed
Task 9
At what time was the malicious file executed?
I obtained the answer to this question while solving Task 7. This information is located in the Prefetch file PARTNERSHIP.PDF.EXE-CCA24020.pf (Fig 9).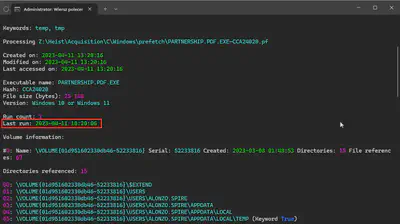
Answer: 2023-04-11 10:20:06
Task 10
The malicious file dropped 2 files on the system which performed further actions on the endpoint. What’s the name of these 2 files? (alphabetical order)
Analyzing the output of the command PECmd.exe -f C\Windows\prefetch\PARTNERSHIP.PDF.EXE-CCA24020.pf, near the end of the results, I found information about two additional exe files (Fig 10).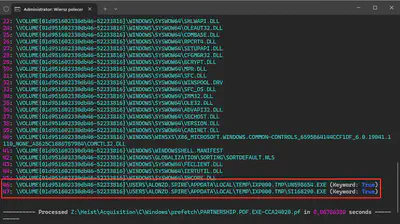
Answer: SI168290.EXE, UN598654.EXE
Task 11
One of the files from Question 10 dropped two more files onto the system. What are the names of these files? (in alphabetical order)
Both previously detected files, since they were executed, also have Prefetch files. I checked them using PECmd.exe. Analyzing the UN598654.EXE file, I found the answer (Fig 11).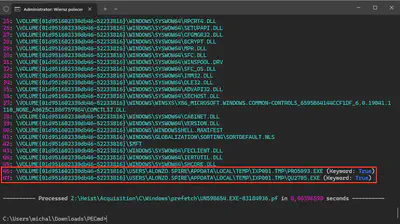
Answer: PRO5093.EXE, QU2705.EXE
Task 12
What’s the malicious C2 IP Address and port?
At first, I tried to find something in the system logs using the Chainsaw tool. Searching through the logs for each of the previously mentioned exe files, I didn’t find anything significant. Therefore, I decided to look at the Heist.pcapng file. After preliminary analysis, it turned out that the largest data exchange was not conducted with the C2 server, which was a dead end. However, knowing the time when the malicious software was executed, I decided to review the communication around that time. The timestamp of packet 110775 and the port initially matched my expectations (Fig 12).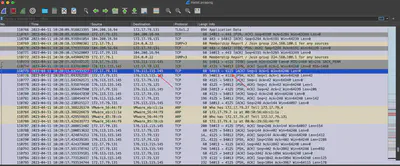
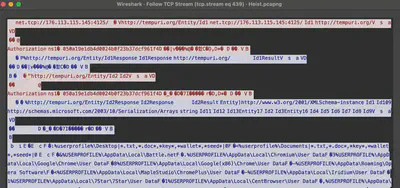
Answer: 176.113.115.145:4125
Task 13
What’s the malware family of the malicious file?
Analyzing the communication between the malicious software and the C2 server, I did not find direct information about the family of this software. Only after searching for the syntax sent by the server http://tempuri.org/Entity/Id1 (Fig 13) did I find the answer on this website.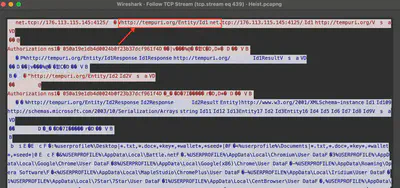
Answer: Redline
Task 14
Which malicious file exfiltrated data from the endpoint?
I have to admit that analyzing the communication was not easy. Using this article, I managed to identify which malicious file established the connection. Information about this is contained in the communication (Fig 15).
Answer: C:\Users\alonzo.spire\AppData\Local\Temp\IXP001.TMP\qu2705.exe
Task 15
What’s the process ID of the malicious file used to exfiltrate data?
At the beginning of the communication, the malicious software gathers basic information about the system and the processes running on it (Fig 16).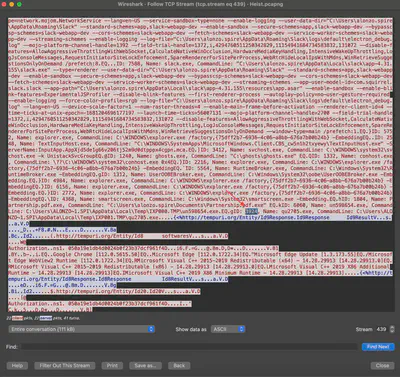
Answer: 3924
Task 16
There was another alert after this incident of data exfiltration from another FTP server hosting critical files. Our TI team believes there may have been an internal credential leak. What’s the IP address and the password of the FTP server which Alonzo had access to?
The stolen IP address and FTP server password are found in the communication with the C2 server (Fig 17).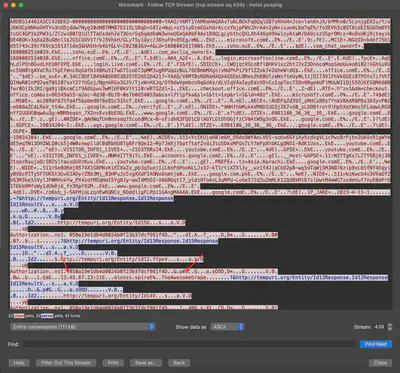
Answer: 13.45.67.23:TheAwesomeGrape
Task 17
What was the password of the YouTube channel which was hacked?
Searching through the communication using the keyword “youtube,” I found the password (Fig 18).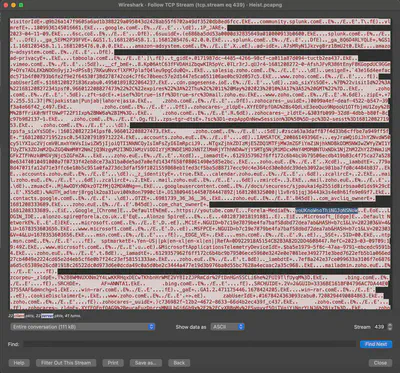
Answer: yoUKnoWnoThiNGJoNSNoW
Task 18
Alonzo reported unauthorized use of his credit card and assumed his card details were stolen. Please confirm his credit card number.
This was not an easy task. To find the stolen credit card number, I thought it would be easier to copy the text to a text editor, such as Sublime, and use regular expressions (regex). A credit card number consists of 16 digits, so I used the regex expression \d{16} and searched the entire text for it (Fig 19).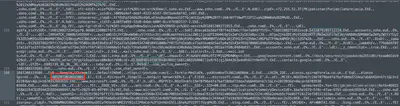
Answer: 4012873018191881
Task 19
A migration plan document was also stolen in the attack which included some sensitive internal information. Who sent the document to Alonzo?
I must admit that this was an interesting challenge. After finding the name of the target file in the communication with the server, it turned out to be a docx file. The rest of the communication was unreadable (Fig 20).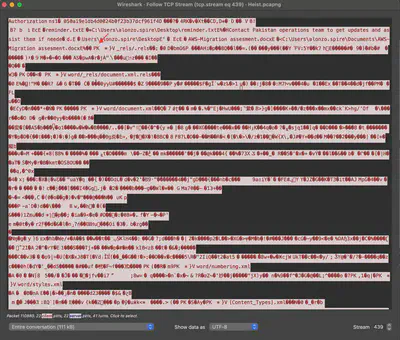

Answer: Abdullah Yasin
Task 20
Forela is planning to upgrade its infrastructure as it is expanding globally. What’s the date when the infrastructure will be upgraded?
I solved this task in the same way as the previous ones. By recovering the Infra upgrade.docx file and reading its content, I found the answer (Fig 23).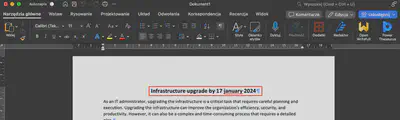
Answer: 2024-01-17
Task 21
How many bytes of data were sent by the malicious process found in question 14? Please note - the PCAP data does not provide the answer.
A small hint for solving this task is in the question - “PCAP data does not provide the answer.” I began looking for the answer elsewhere. Initially, grep results yielded nothing, so I started reviewing what other files I received to solve the task. In the C\Windows\System32\SRU\ directory, I found the SRUDB.dat file, which is responsible for collecting diagnostics from the Windows system. I thought this might be a good direction. Using the command SrumECmd.exe -f "C\Windows\System32\SRU\SRUDB.dat" -r "C\Windows\System32\config\SOFTWARE" --csv ., I converted the data contained within it to CSV files. I then opened the file 20240812173827_SrumECmd_NetworkUsages_Output.csv in Excel and searched its contents for the malicious software. In the BytesSent column, I found the answer (Fig 24).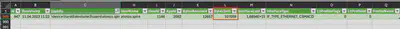
Answer: 107059