HTB Sherlock - BOughT Writeup
 HTB Sherlock - BOughT Writeup
HTB Sherlock - BOughT WriteupSherlock Scenario
A non-technical client recently purchased a used computer for personal use from a stranger they encountered online. Since acquiring the computer, the client has been using it without making any changes, specifically not installing or uninstalling any software. However, they have begun experiencing issues related to internet connectivity. This includes receiving error messages such as “Server Not Found” and encountering difficulties with video streaming. Despite these problems, checks with the Windows Network Troubleshooter indicate no issues with the internet connection itself. The client has provided a memory image and disk artifacts for investigation to determine if there are any underlying issues causing these problems.
Artefacts
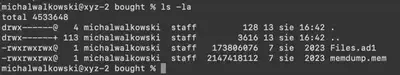
After unpacking the received ZIP archive, we get two files (Fig. 1):
Files.ad1- contains logical copies of digital evidence, such as selected folders, files, or partitions from computer systems, collected during the forensic process. Unlike full disk images, .ad1 files may contain only selected data fragments, allowing for more efficient storage and analysis of specific evidence without needing to copy the entire disk,memdump.mem- a RAM dump from the compromised computer; I have frequently encountered such files when solving Sherlocks.
Solution
Task 1
What is the best volatility profile match for the memory image?
Using the command python vol.py -f ../htb/memdump.mem imageinfo, I obtained basic information about the provided memory image. Among the data are the detected profile and the time of the image capture (Fig. 2).
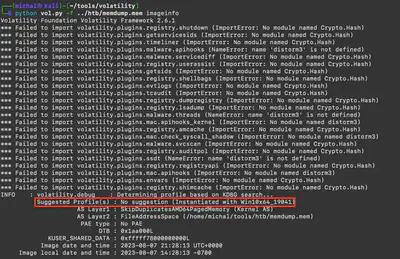
Answer: Win10x64_19041
Task 2
When was the image captured in UTC?
The answer was obtained by solving Task 1, from the same command output (Fig. 3).
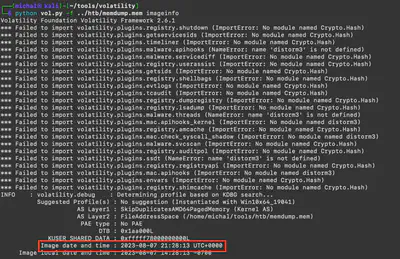
Answer: 2023-08-07 21:28:13
Task 3
Check running processes and confirm the name of the suspicious running process.
Using the command python vol.py -f ../htb/memdump.mem --profile=Win10x64_19041 pstree, I listed the processes running at the time of the memory dump. Reviewing them, I noticed a suspicious process named SecurityCheck, which was running the subprocess conhost.exe (Fig. 4).
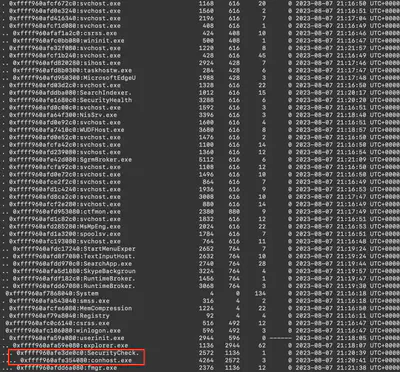
Answer: SecurityCheck
Task 4
What is the full path of the malicious process?
Knowing the name of the malicious process, I used the command python vol.py -f ../htb/memdump.mem --profile=Win10x64_19041 cmdline | grep SecurityCheck to find the path from which it was launched (Fig. 5).
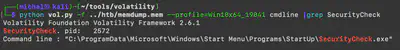
Answer: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\SecurityCheck.exe
Task 5
What is the sha256 value of the malware?
Instead of trying to extract the malware from the memory dump, I decided to first export this file from Files.ad1. I used FTK Imager to open the file. Knowing the location of the file, it was easy to find it (Fig. 6).
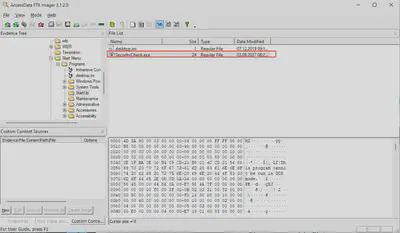
Files.ad1 using FTK Imager.
After successfully exporting the file, I used the command shasum -a 256 SecurityCheck.exe to compute its hash (Fig. 7).
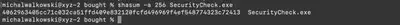
Answer: 4062963405cc71c032ca51ffd409e832120fcfd496969f4ef548774323c72413
Task 6
What is the compilation timestamp for the malware?
For further analysis of the malware, I used VirusTotal. There, I found the answer to this question (Fig. 8).
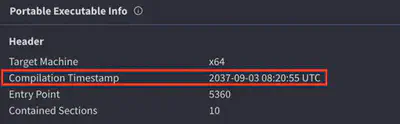
Answer: 2037-09-03 08:20:55
Task 7
What is the name of the mutex that the malware creates?
I also found the answer to this question using VirusTotal (Fig. 9).
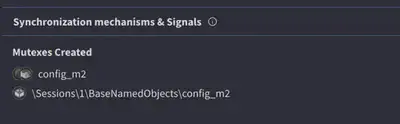
Answer: config_m2
Task 8
At the top of the main function which anti-debugging function is being used?
To analyze the SecurityCheck.exe file, I used Ghidra. I admit the question was a bit confusing as it suggested that the function was directly in the main function call. However, after locating the entry function, it turned out to branch out into other sub-functions. A quicker approach to finding the anti-debugging function was to check which libraries and functions the program imports. Reviewing the imports, I noticed that the program imports the IsDebuggerPresent function from kernel32.dll. I then confirmed that this function is called in the code (Fig. 10).
Answer: IsDebuggerPresent
Task 9
How many minutes does the malware sleep before calling the above anti-debugging function?
In Fig. 10, line 31, before calling the IsDebuggerPresent function, a sleep function is called with a value of 900,000 milliseconds, which converts to 15 minutes.
Answer: 15
Task 10
This malware uses DGA, how many unique C2 domains in total is this DGA capable of generating?
Since I do not deal with malware analysis on a daily basis, I first had to learn what DGA stands for. DGA (Domain Generation Algorithm) is an algorithm used by malware to generate a large number of potential domain names (C2, or Command and Control) based on certain rules. These domains are then used by the malware to communicate with command servers, such as issuing commands, stealing data, or updates.
After familiarizing myself with the definition, I knew what to look for. After a brief search, I found a for loop responsible for generating domains. To simplify the analysis, I renamed some variables (Fig. 11). The for loop starts from 0 and has a stopping condition less than 6, which means it will execute 6 times (line 35). In line 39, a function returning a pseudo-random value is called, and then in line 41, a modulo 9 operation is performed. This means that a number from 0 to 8 is randomly selected. To make the situation more complex, line 43 has an if (tmp_i == 2) condition that selects a constant value. In summary, the function only randomly selects 5 places out of 6 possible. This can be simplified to the equation: (95 = 59049).
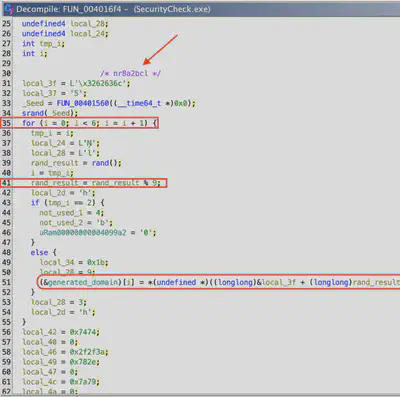
Answer: 59049
Task 11
How many unique C2 domains start with “rb”?
Knowing the DGA generation algorithm, it is enough to adjust the condition. Since two letters are fixed, by taking this into account and reducing the exponent by 2, I obtained the correct result: (9(5-2) = 729).
Answer: 729
Task 12
How many unique C2 domains end with “rla”?
Similarly, having three fixed characters, I reduce the base exponent by 3, resulting in (9(5-3) = 81).
Answer: 81
Task 13
Which file is being used to store the active C2 domain?
In the main function of the malware, there are two file paths from which the software loads the configuration (Fig. 12).
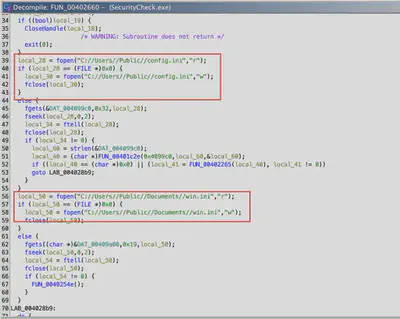
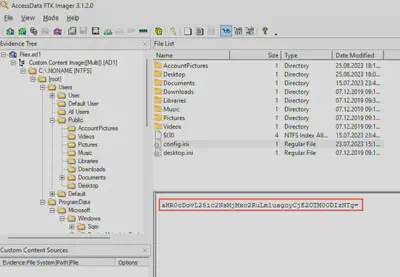
To confirm which one is used, I decided to take a shortcut and checked if these files were present in Files.ad1 along with the configuration. Both were available. The information recorded in the win.ini file confirmed that this is where the current C2 domain value is stored (Fig. 13).
Answer: C:\Windows\win.ini
Task 14
Which file is being used to store commands from the C2 server?
During Task 13, I checked both files. It turned out that the second file contained the commands received from the C2 (Fig. 12).
Answer: C:\Users\Public\config.ini
Task 15
What was the active C2 FQDN at the time of artifact collection?
The name of the active domain recorded in the configuration file was found while working on Task 13 (Fig. 13).
Answer: http://cl0lr8.xyz
Task 16
How many kinds of DDoS attacks can this malware perform?
Analyzing the software, I encountered a function that defines two attack types. The first type, labeled as type 1, is implemented using the PING system command. The second type of attack involves sending HTTP GET requests. In the screenshot below, I have adjusted the names of some variables and function calls to improve readability (Fig. 14).
Answer: 2
Task 17
What is the FQDN of the target website?
During Task 13, I found the configuration file responsible for storing commands received from the server. The information contained in this file was base64 encoded (Fig. 15).
After decoding it with CyberChef, I obtained the answer (Fig. 16).
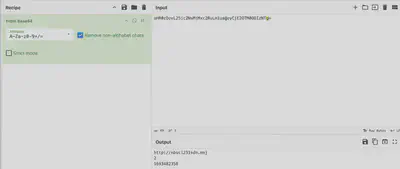
Answer: http://nbscl231sdn.mnj
Task 18
What was the expiration date for the active attack at the time of artifact collection in UTC?
In the decoded configuration file, the last line contains the timestamp 1693482358. I converted it to a date using this site.
Answer: 2023-08-31 11:45:58
Task 19
How many GET requests does the malware perform against the target domain before sleeping for a while?
In the same function where I identified the attack types, there is a for loop that executes 20 times. Inside this loop, the function send_get_request is called, which, after detailed analysis, sends a GET request only once. After the loop completes, the sleep function is called (Fig. 17).
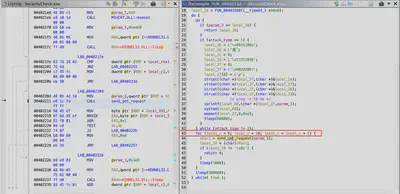
for loop responsible for HTTP GET requests.
Answer: 20
Task 20
There seems to be another attack method with ICMP requests. How many of these requests can the malware send before sleeping for a while?
When selecting attack type 1, you can see a call to the strcat function, which is used to concatenate strings. After concatenating all fragments, you get the command ping -n 16 %s. This command is then passed to the system function, which executes it on the operating system (Fig. 18).
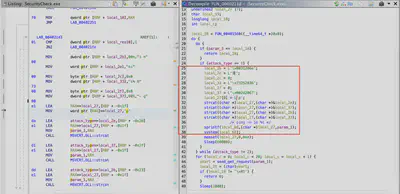
Answer: 16
Task 21
Is this malware prone to Botnet hijacking?
Looking at how the malware communicates with the C2 server and how it saves configuration files, I believe the malware is definitely prone to hijacking. :)
Answer: yes