Phishing on the lock screen: how a fake Windows 11 page helped capture a user's password during a red team test
 Phishing on the lock screen
Phishing on the lock screenDuring one of the Red Team projects, we gained access to a computer in the client’s network using TeamViewer as an entry point to their infrastructure. However, we didn’t have the user’s password for the account we were working on, so every time the computer locked, we had to ask the client to unlock it. The lack of this password also caused other issues, so I decided to use a bit of social engineering to acquire the necessary credentials.
After a brief research, I discovered that a similar idea had already been implemented. The inspiration for my attack was a project available on GitHub at this link. The main difference was that the page in the repository mimicked the Windows 10 lock screen, while I had access to a Windows 11 machine. The lock screens of both systems differ slightly (fig. 1)—and it’s not just about the wallpaper, which can be easily customized or replaced. Therefore, I decided to create my own version of the page imitating the user’s lock screen.
For the attack to succeed, the captured password had to be either saved locally in a location known only to me or sent to my C2 server. I chose the second option. To avoid issues with special characters in the password, I encoded it in Base64 before sending it. Additionally, to ensure the user entered the password correctly, the page always displayed an error message on the first attempt. Only on the second attempt did the login screen close.
The final step, besides a bit of luck, was to launch the page in so-called kiosk mode. This mode allows a webpage to be displayed in full-screen view without any browser interface elements. You might associate kiosk mode with various public devices, such as information kiosks. However, there was a significant problem: in the provided repository, kiosk mode relied on specific commands in CMD or PowerShell, which were blocked on the client’s machine. I managed to bypass this limitation by creating a shortcut on the desktop with the appropriate launch parameters.
Figure 2 shows the real lock screen of a Windows 11 user.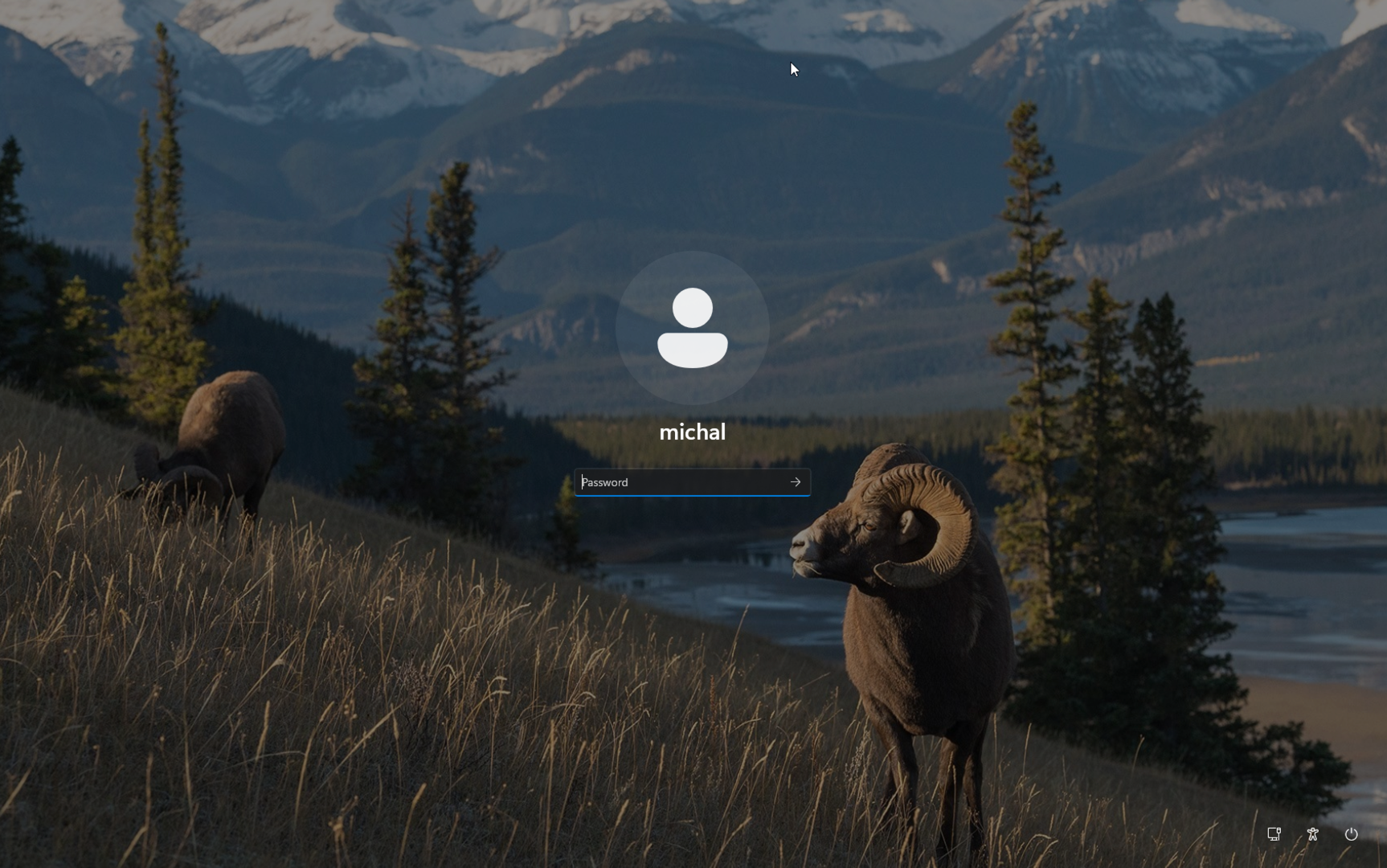
Figure 3 shows the fake lock screen I created. It lacks several elements, such as the icons in the bottom-right corner. I couldn’t find satisfactory graphics for these, so I decided to remove them. As it turned out later, their absence didn’t affect the overall success of the attack.
Below, you can watch a video showcasing this attack in action.
In conclusion, the presented technique proved effective. I successfully captured the user’s password, allowing us to proceed to the subsequent stages of the project.