Introduction to Penetration Testing – Overview of the Burp Suite Tool
In this post, I will focus on one of the most important tools used in penetration testing — Burp Suite. I will discuss its features that support the process of identifying vulnerabilities in web applications and explain how this tool can assist in security analysis.
 Introduction to Penetration Testing – Overview of the Burp Suite Tool
Introduction to Penetration Testing – Overview of the Burp Suite ToolWhat is Penetration Testing?
Penetration testing, also known as pentesting, is the process of conducting controlled simulated attacks on IT systems to identify their weaknesses and assess their current level of security. Pentests aim to detect potential threats that could be exploited by cybercriminals to gain unauthorized access to the system.
A pentester checks, among other things, whether:
- a user of the application can access another user’s data, even though they shouldn’t,
- a user can gain higher privileges that are not intended for them,
- there is a risk of unauthorized takeover of the administrator’s account.
Essential Tools in Penetration Testing
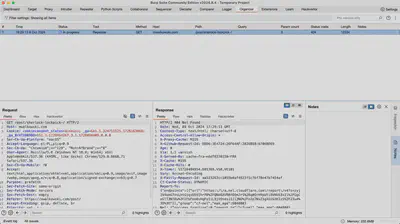
One of the tools used for conducting penetration tests is Burp Suite, a comprehensive environment that supports the analysis of web application security. Burp Suite offers a wide range of features that enable effective identification of vulnerabilities and analysis of communication between the browser and the server. The tool is available in two versions:
- Community Edition - a free version that provides basic features suitable for beginner users.
- Professional Edition - a paid version with advanced features that support comprehensive analysis and test automation (including a built-in scanner).
Burp Suite Features
Target Tab
The Target tab allows for detailed mapping of the application by creating a sitemap that contains all the resources available in the tested application. This is a crucial element in the initial phase of penetration testing, enabling the analysis of the application’s structure and identification of potential attack vectors.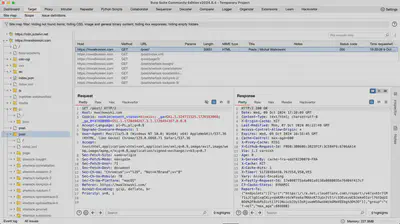
Proxy Tab
The Proxy tab in Burp Suite allows for the interception and modification of HTTP and HTTPS requests that are transmitted between the browser and the server. With this feature, I can manipulate the data sent in the requests, which is highly useful in analyzing vulnerabilities such as Injection or Cross-Site Scripting (XSS).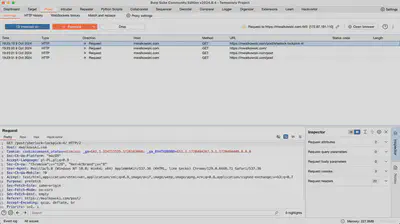
Repeater
Repeater is a feature that allows the repeated sending and modification of HTTP requests to test various scenarios and analyze server responses. This tool is particularly useful when investigating complex attacks like SQL Injection, where each change in the request can lead to the discovery of new information about the system.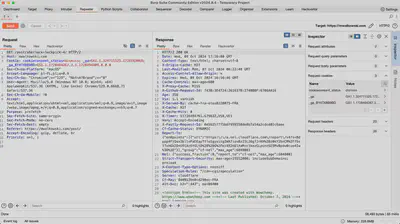
Intruder
The Intruder tab is used to automate attacks on web applications, such as brute-force or fuzzing. It allows for defining injection points in requests and testing various values to find vulnerabilities or exhaust the application’s defenses.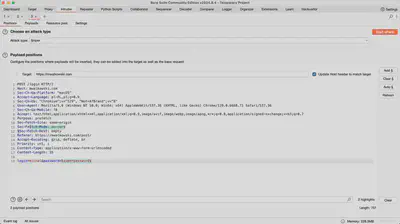
Sequencer
The Sequencer tab allows the analysis of the entropy and randomness of data generated by the application, such as session tokens or cookies. This helps determine whether the data is sufficiently random to prevent token prediction attacks.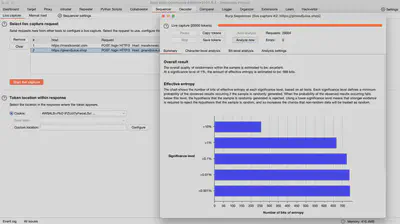
Decoder
The Decoder tab enables the encoding and decoding of various data formats, such as Base64, URL encoding, ASCII, or hex. It is a useful tool for data analysis and manipulation during penetration tests.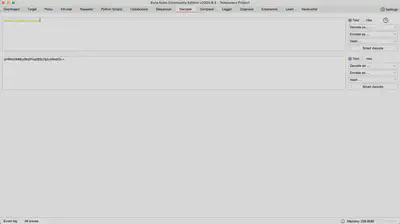
Comparer
Comparer is a tool for comparing data that helps identify differences between two requests or responses. It can be used to analyze subtle variations that may indicate vulnerabilities or unintended application behaviors.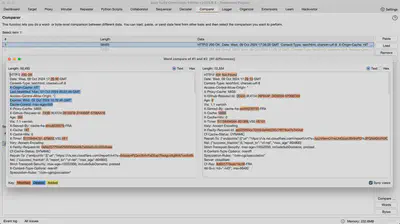
Extender
The Extender tab allows adding plugins to Burp Suite, which extend its functionality. This enables you to customize the tool according to your needs and integrate it with additional modules that facilitate the detection of specific vulnerabilities.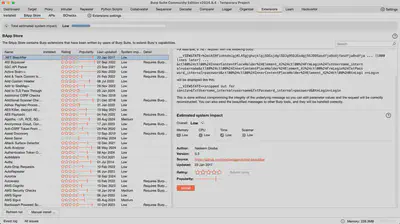
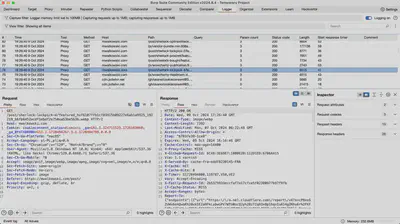
Logger and Organizer
The Logger tab tracks all the requests that have passed through Burp Suite, regardless of their source. The Organizer supports effective task and note management, making it easier to track progress in long-term testing projects.